As the number of highly-targeted, fraud-based email attacks on employees continues to rise, what if there was a way to forecast when the next one will hit their inboxes? As it turns out, there very well may be.
In case there was any remaining doubt that data science is cool, recent analysis from Agari researchers studying emerging patterns in email fraud may forever put that doubt to rest.
In fact, their findings may represent a breakthrough that could soon enhance the Agari solutions organizations rely on to repel business email compromise (BEC) and other advanced email threats. How? By using artificial intelligence to predict when the next malicious email is most likely to hit.
It couldn't come a moment too soon. As it stands now, email fraud will cost US businesses more than $12 billion in losses this year. In fact, despite spending billions of dollars on cybersecurity, most businesses remain wide open to email attacks that leverage advanced forms of identity deception to bypass traditional security systems by exploiting the weakest link in cyber-defenses: Human beings.
Through meticulous targeting and social engineering, these malicious emails fool recipients into revealing sensitive information or sending payments to criminals by making recipients believe they're responding to a trusted colleague or business. Traditional email security tools can't detect these messages because there's no malware to detect, no easy giveaways in the code, and nothing apparently suspicious about the message.
But we've discovered an emergent pattern that could offer clues to new ways to fight back. In part one of this series, we'll discuss our findings. In parts two and three, we'll take a forensic look at our methodologies to help explain how we arrived at a rather surprising conclusion—and what it could mean.
Hidden Figures
For those just tuning in, Agari's machine learning, AI-based solutions protect organizations from email fraud by going beyond content analysis and sender infrastructure reputation to assess people, relationships and behaviors in order to stop attacks from ever reaching their targets.
In order to do that, our data scientists are continuously fine-tuning data models to account for new criminal tactics and technologies. As part of that effort, we recently set out to investigate whether the propensity to receive malicious emails is a product of time, or merely the total volume of emails an organization receives.
The idea: Identify whether we can predict (a) the time before an organization will receive a malicious email and (b) the number of "good" or legitimate emails they will receive before that next malicious one. Along the way, we might confirm whether larger organizations, which receive more email, are more likely to be exposed to email attacks overall.
Time is of the Essence
To answer these questions, we plotted time- and email-volume gaps, and ran statistical analysis on the 2 trillion emails Agari monitors in a given year.
As it turns out, malicious email volume did not correlate with total email volume. Malicious emails could arrive in succession, or there may be thousands of legitimate emails before the next malicious one arrives, regardless of the overall amount of email an organization receives.
There were, however, intriguing patterns in time gaps. These gaps, we found, were predominantly small. The average was 6 minutes between malicious emails, with 90% falling within a 16-minute window.
That doesn't mean we can project that the time gap between malicious emails will be every 6 minutes with any confidence. This is just the average across time, with some intervals very small, and others quite large. So it's not representative of any underlying pattern in and of itself.
What is surprising: This same average time gap between malicious emails exists in every organization we studied.
To be clear, the intervals themselves are not uniform between organizations—in fact, they vary widely. Nonetheless, however they differ, they all share this same average overall time gap. And it doesn't matter whether it's an SMB or a global enterprise.
Minding the Gap
In order to better understand what this might mean, we analyzed the distribution of malicious emails and compared this to ordinary email delivery patterns.
As you might expect, overall email volumes have a clear pattern of peaks during workday hours and troughs over the weekends and evenings. The visual below shows the total volume of emails received at one organization every minute over a 45-day period.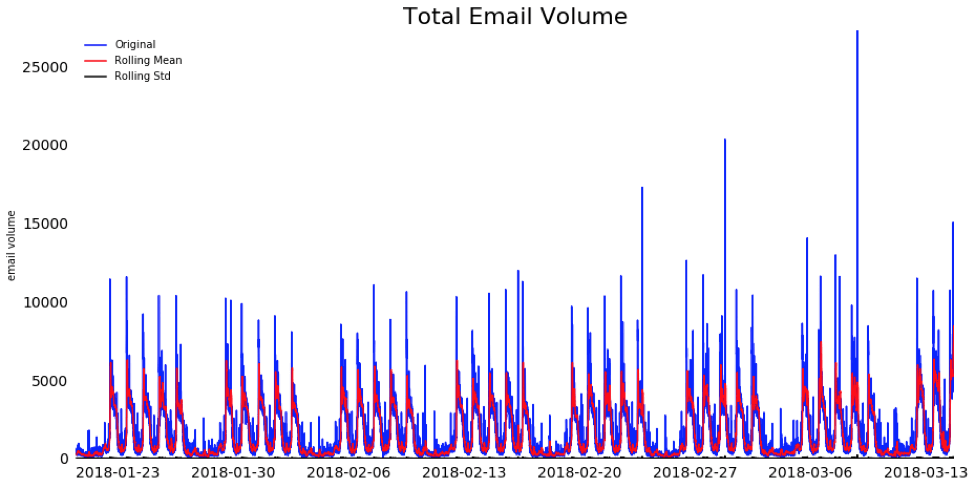
But those patterns are less evident in malicious email volume cycles, shown below.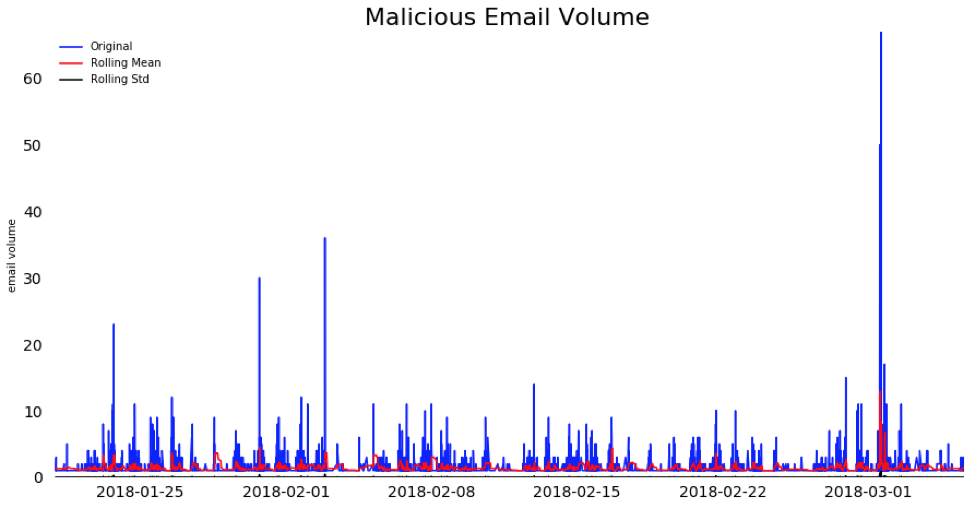
As you can see, there are spikes in the volume of malicious emails, and they are coming in successively in batches followed by a brief pause. Unlike normal email volume these spikes do not mimic work hours or correlate with total email volume. The mean and variation of the malicious emails are, on average, fairly consistent over the 45-day period—regardless of weekdays or work hours.
And the time gap between each malicious email: That same 6 minute average.
What does this mean? Irrespective of email volume or activity at an organization, malicious emails are being delivered to employee inboxes every few minutes on average—and this is the case for all organizations, small and large.
This is happening to every organization we studied, and, as you can see, with increasingly predictable frequency. The attacks will no doubt be sustained in the months and years ahead.
Training employees to increase awareness of advanced email attacks can certainly help, but it's important to recognize at the same time that 1) these messages are so well-executed they are becoming increasingly more difficult to recognize, and 2) training employees to innately distrust their inbox will likely have a negative impact on productivity.
Ultimately, it's safe to presume that your organization will be targeted by advanced email attacks and that eventually, even well-trained individuals are going to be fooled. This makes the best defense preventing malicious emails from ever reaching their target, which is precisely our mission here at Agari!
Part 1 of a 3 part series
Next up: In part two, we'll delve into predictive models for malicious emails and how these may shed light on what underlies the patterns of malicious emails we have uncovered here.