Are you ready for Binding Operational Directive 18-01? On October 16, 2017, the Department of Homeland Security (DHS) issued this directive in order to implement better security protocols on government emails. The DHS BOD 18-01 is a compulsory directive to all federal departments and agencies. Among the measures mandated in BOD 18-01 is a requirement that federal agencies adopt Domain-based Message Authentication, Reporting & Conformance, or DMARC, to prevent spoofing of federal government domains in email. This will reduce phishing of citizens and other federal agencies.
Federal Government agencies are vulnerable to email fraud because over 80 percent of federal domains currently lack DMARC protection entirely. This vulnerability leaves their constituents exposed to phishing and other forms of email attacks that impersonate their agency email domains. Cybercriminals exploit this vulnerability by sending billions of spear phishing emails per year claiming to be from these government agencies. When fully implemented, DMARC virtually eliminates emails that impersonate an agency domain.
Federal departments and agencies have 30 days to submit a plan of action, 90 days to implement at least the lowest level of DMARC (monitoring, or p=none), and one year to implement the highest level of DMARC (reject, which prevents delivery of any unauthenticated message). Each month, Agencies will also submit monthly status updates to show how the project is progressing.
This is a very aggressive timeline to meet BOD 18-01. In order to meet this timeline, Agari recommends that all federal agencies get started immediately. Check out the guide to creating an Agency Plan of Action and the template for an Agency Plan of Action to get started today.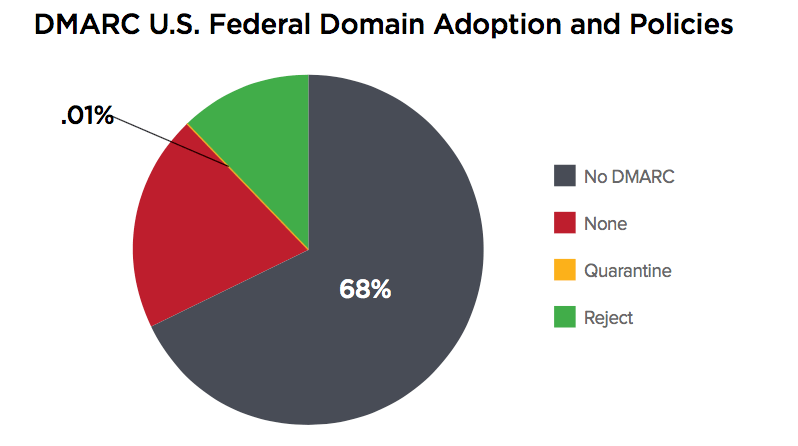
For email security, DHS will require the use of STARTTLS, which signals to a sending mail server that encryption of the email in transit is possible.
SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) are also to be implemented and are important elements of DMARC. These technologies allow a sending domain to authenticate emails and thus make unauthorized emails easier to spot.
The process of moving to p=reject can be challenging to do as a DIY project. Agencies often roll this out in phases to avoid negatively affecting email deliverability. They also often engage an email security solution and service provider to help ensure that there are no errors in the rollout and to get additional Forensic data not available as part of the DMARC specification.
DMARC is designed to be deployed in stages. Companies generally start in “monitor mode” using a “p=none” policy. This policy provides feedback about servers using the domain name in the “From:” header of the email messages they send. The domain owner uses this information to make adjustments to their SPF and DKIM configurations until all of their legitimate mail sources are properly authenticated. Aggregate DMARC reports are also provided to the agency and can make agencies aware of the source of unauthorized emails to continually improve email security.
At this point, the policy can be tightened to “p=quarantine,” which sends authenticated messages to the recipient’s spam folder. Organizations often roll out DMARC across domains on a test basis, so they start with a subset of email traffic and then eventually roll it out to more and more domains and inboxes.
Upon meeting binding operational directive 18-01, federal organizations will have DMARC set to reject (p=reject), which will only allow authenticated and trusted emails to reach the inbox and will block all other email.
DMARC is designed to:
- Minimize false positives
- Provide robust authentication reporting
- Assert sender policy at receivers
- Reduce successful phishing delivery
- Work at Internet scale
- Minimize complexity
Finally, it is important to realize that email service providers must also deploy DMARC on the receiver side. Currently, the major email service providers—Microsoft, AOL, Google and Yahoo!—have deployed DMARC, but smaller email service providers, self-hosted email servers or government-hosted servers may not provide the same level of protection.
Agencies that pioneered DMARC in the federal government include the U.S. Senate, the Department of Health and Human Services, Customs and Border Protection, the U.S. Census Bureau, the Department of Veterans Affairs and the U.S. Postal Service.
The Department of Homeland Security’s BOD 18-01 is intended to protect federal agency emails from being exploited by cybercriminals. The relatively short timeline for compliance will require agencies to implement STARTTL and DMARC email authentication features simultaneously.
Agari is a leading cybersecurity company that currently monitors over 400 government domains protecting against cybercriminals who use false identities to commit fraud, steal information and undermine trust. The Agari Email Trust Platform is the industry’s only artificial intelligence (AI) driven defense system that models authentic, trustworthy communications in order to protect humans from being deceived by cyber attacks such as phishing, ransomware and business email compromise (BEC).
To learn more about how Agari can help government agencies comply with the 18-01 directive, visit Contact us.