The allure of airline status and points, along with the abundance of personally identifiable information (PII) of customers and employees, make the airline industry a prime target for threat actors on the dark web. Depending on the goal of the actor and the nature of the stolen data, criminals can find airline-specific materials for sale on a variety of markets.
Nick Oram, security operations manager for Dark Web & Mobile App Monitoring Services at Fortra, recently spoke with ConsumerAffairs about the scope of airline PII vulnerable on the Dark Web. “PII associated with these accounts can include items such as username, password, address contact/info, credit card details, passport details, reward points, etc.,” explained Oram. “There are hundreds of areas where account data can be sold, and content is updated daily as threat actors continue to supply new data.”
Below, we take a look at the types of threats targeting airlines and their customers on dark web marketplaces, and what organizations can do to prevent exposure and attacks.
Marketplaces that specialize in the sale of account credentials are havens for threat actors interested in exchanging compromised information. In these marketplaces, stolen customer account information is in steady supply, as threat actors are consistently adding new data acquired through network compromise and phishing scams. This data is often sold for minimal fees, allowing threat actors of all levels of experience to use for the malicious purposes of their choosing.
Threat Types
Account Data
Account data associated with specific airline providers is commonly advertised with varying levels of access on dark web marketplaces. Below is an example of data attributed to the Turkish Airlines brand. This particular data set contains customer names, points available on accounts, and print screens showing the account actively logged into. By capturing this intelligence, security teams can identify compromised customers without purchasing the data directly off the marketplace.
Overview of Available Account Data for Turkish Airlines
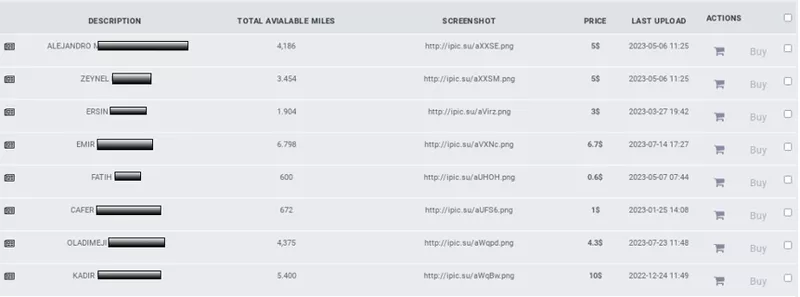
Account Data for Sale
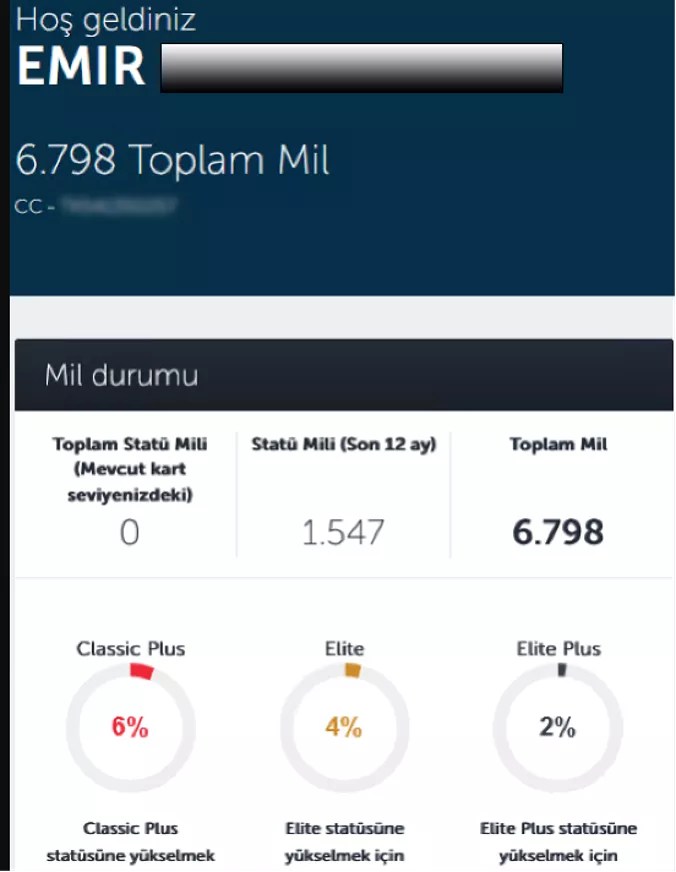
Print Screen of Airline Account for Sale
Airline Status
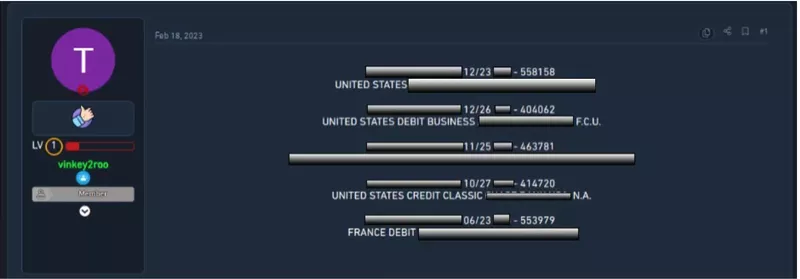
Threat actors will frequently look to purchase different levels of status for well-known airline brands. Not only do members of the dark web advertise their stolen data for sale, but individuals also broadcast their preferences of information to buy. In this type of exchange, threat actors will typically provide the best method of contact in posts on dark web forums.
In the example below, the threat actor is instructing potential sellers to reach out via the chat messaging platform for sales inquiries.
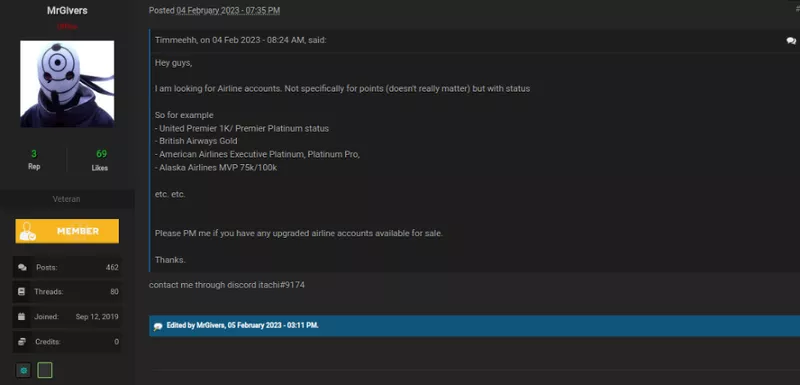
Card Data/Credit Unions
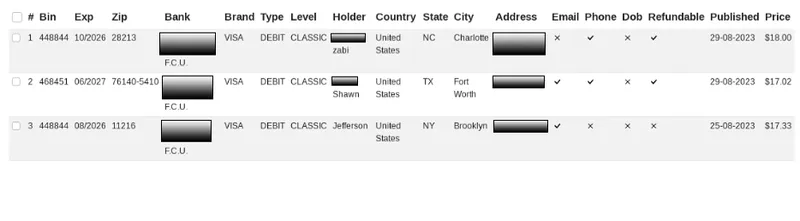
Credit unions associated with the airline industry are also targeted on the dark web. The sale of member credit/debit card data can be found in varying levels of detail on both carding marketplaces as well as forums. This type of information can be obtained by threat actors through malicious means such as skimming devices, point-of-sale malware, and sniffers.
Below are two examples of card data targeting an airline’s credit union branch. The data from the first screenshot showcases customer PII tied to the account on a typical carding marketplace. The second displays full credit card numbers posted over a carding forum.
Database Leaks
As with other industries, airline customers and employees are not immune to data leaks being posted on the dark web. Data leaks can be advertised by threat actors for a fee, with the stolen data, or the fully compromised credentials posted for free.
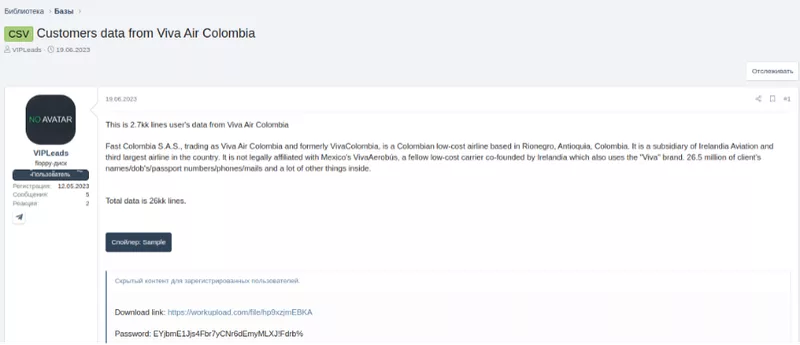
The screenshot below showcases two Colombian airlines with various customer data exposed. The types of information include: user data, name, date of birth, passport numbers, phone, email, and more.
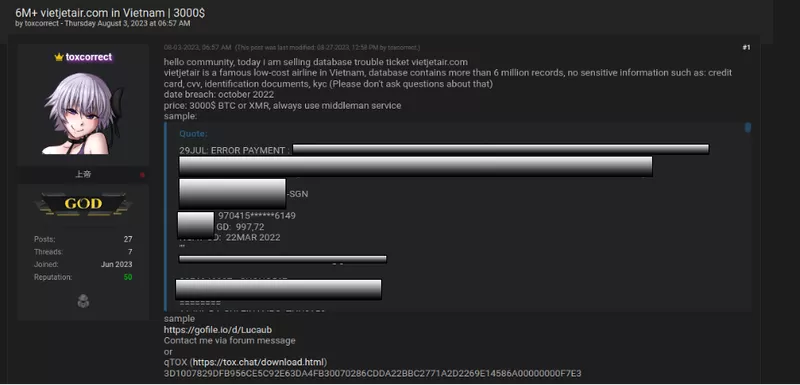
It is commonplace for threat actors to post small samples or highlights from the stolen data on dark web forums. The purpose of this is to entice members to reach out via private message in regards to procuring the information. In the screenshot below, the threat actor gives examples of the types of information included in a small database compromised directly from a company server.
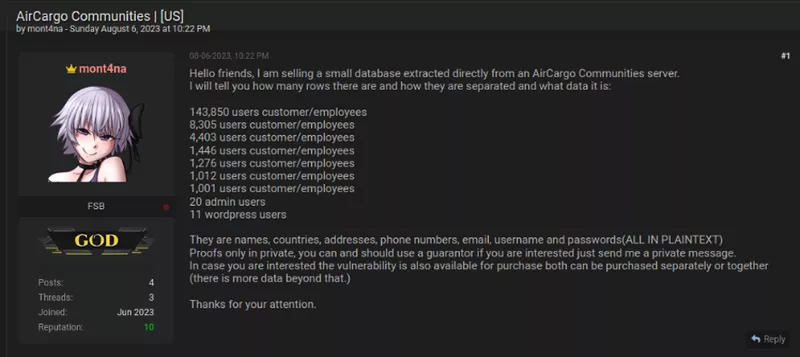
Below, in the same forum, the threat actor has posted samples of the data in addition to offering the total database for a fee of $3,000 USD.
Infostealers
In addition to purchasing sensitive data, infostealer data has been a popular vector for threat actors to gain internal access to companies and should be considered a high-priority security threat. Infostealers are a type of malicious software commonly used to exfiltrate data from infected computers. This information is then sold to other criminals, who abuse company credentials to infiltrate network systems.
Threat actors also purchase infostealer malware and launch attacks themselves.
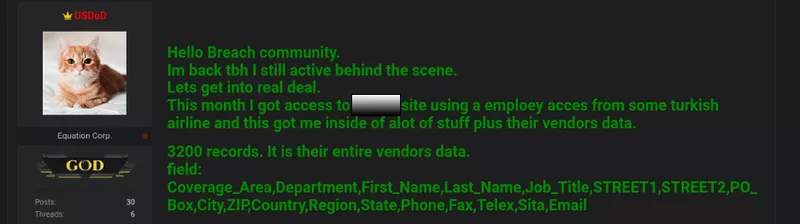
Below is an example of an airline database compromise affecting 3,200 vendors due to a Redline infostealer infection. In this instance, the target of the attack was an airline employee with third-party access to internal systems. The leaked information included names, addresses, phone numbers, and email addresses.
Redline, along with many infostealer malware variants, can be distributed to victims via traditional phishing methodologies, mobile applications, and pirated materials that will infect devices with malicious software when it is downloaded.
Infostealers continue to be a popular method for threat actors to infiltrate an institution’s internal environment or gain access to their customer’s information. Compromised data as a result of an infostealer attack can be purchased for a very small fee and manipulated by the purchaser for their needs.
For instance, infostealer malware can go beyond access to the username and password of the compromised account to capture authentication cookies/tokens of the compromised machine. This allows a user to remain logged into online services without having to constantly sign back in with their password or a two-factor authentication code.
By using session cookies/tokens within their own browser, the buyer is able to bypass security protection measures like two-factor authentication and remain undetected by the compromised user.
Ransomware
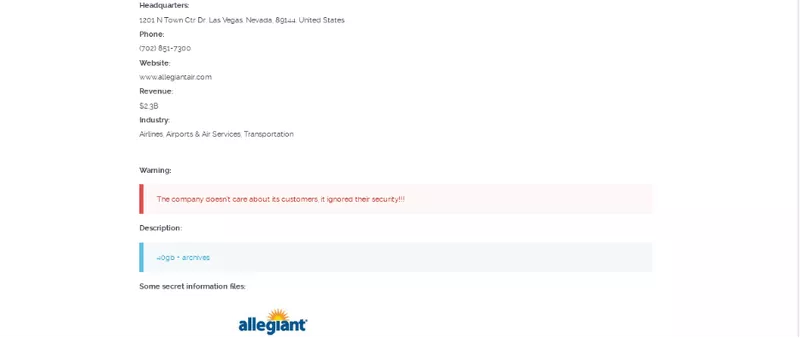
The airline industry continues to be targeted by ransomware groups. Many of these groups have leak sites on the dark web where they will publicly shame compromised corporations. These sites include countdowns documenting the time to pay ransom before data is leaked, samples of the data, screenshots of documents that were compromised, and download links to get the full set of data.
The example below advertises compromised data belonging to Allegiant Air on a Clop ransomware group leak site.
The dark web is ripe with marketplaces distributing stolen information and the tools needed to target and attack vulnerable industries. Account data belonging to the airline sector is highly sought after and available through these marketplaces, where cybercriminals advertise varying types of stolen information for relatively small fees.
While the dark web can be difficult to navigate, security teams should familiarize themselves with spaces where compromised information associated with their brand may be present. By proactively identifying data linked to their brand, customers, employees, or partners, they will have the opportunity to limit or contain any damage that could occur as a result of compromise.
Learn how Fortra’s PhishLabs can help identify malicious activity targeting your brand on the dark web.
