After barely registering a pulse last year, W2-based business email compromise (BEC) scams are back with a vengeance thanks to coronavirus-related business upheaval.
With the 2019 tax filing deadline pushed back to July 15, 2020, and as much as 66% of all corporate employees working from home, operations for many companies have been anything but business as usual. Still we are surprised to see a marked uptick in the number of social engineering schemes aimed at pilfering W2 information in recent weeks.
The W2 form, which US-based businesses distribute to employees, must be included with filed income tax returns. It documents earnings, tax withholding, Social Security number, and other sensitive information. This important information is all an attacker needs to file fake tax returns. Or, they can sell it to identity thieves on the dark web.
W2 Fraud in 2019? Almost Didn’t Exist
As I posted last year, 2019 was an outlier in terms of W2 fraud. In years prior, BEC actors regularly targeted organizations with the intent to con recipients in accounting, HR, or payroll into divulging the highly-sensitive information contained on these forms. But last year, these scams dropped to just 2.5% of all BEC attacks.
While threat actors known to collaborate with the email crime ring we call Scattered Canary had difficulty cashing out on W2 info in 2017, there was still a robust black market for this kind of information heading into the 2018 tax season.
Over the last few years, crackdowns by the IRS, state tax agencies, and the tax-preparation industry may have elevated awareness among potential targets enough to crater W2 scam success rates to the point that cybercriminals moved on to other rackets. That is, enough complacency set in.
2020: The Comeback Scam of the Year
Looking back at state and federal guidance leading into the 2020 tax season, there were far fewer warnings about BEC actors asking for W2 forms from targeted organizations than in 2019. By January, the coronavirus outbreak and resulting tsunami of related phishing ploys focused the attention of security firms and law enforcement elsewhere.
By May, alarming news headlines may have inspired enough vigilance toward COVID-19 related email schemes that some fraudsters may have begun wondering if a simple request for W2 information might bamboozle distracted employees.
If the increased activity we're seeing is any indication, they were right. Today, BEC actors are once again posing as CFOs or other senior executives in emails requesting W2 information for all of a company's employees. Check out this screenshot of an attempt from May 11:
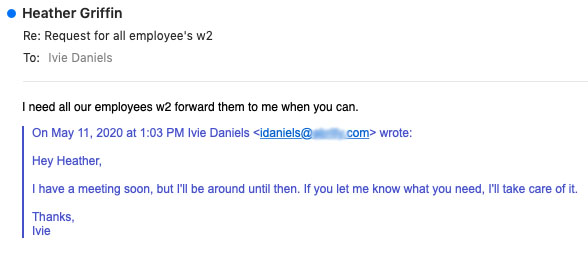
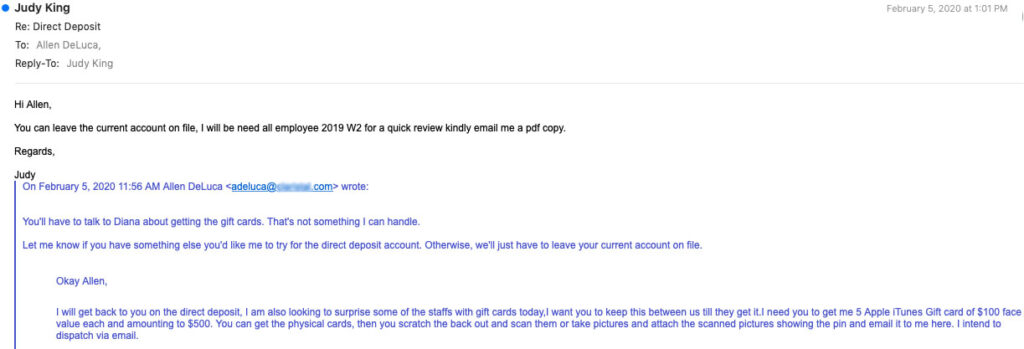
In fact, some actors began sending test campaigns at the end of January. During a covert Agari engagement with a fraud group on February 5th, an email scheme that started as a direct deposit ruse turned into a gift card swindle before morphing into an attempt to steal W2 forms, all in less than three hours.
Extended Tax Season Mean More Time to Attack
Over the last month, we've seen a steady increase in the number of BEC actors requesting W2 information during these covert engagements. With tax filing in the United States extended to July 15 due to COVID-19, perpetrators have more time to filch W2 forms for the current tax season.
Specifically, many attackers are interested in obtaining 2019 W2 information compiled into a single PDF file. Many HR platforms are able to bulk-export W2s for all employees in this form, and this is exactly what actors are seeking.
Once obtained, this information can either be sold or used within the group's immediate network to commit numerous forms of fraud. In some cases, the group has operationalized these crimes: W2s are split into batches of 50 or 100 and are divvied out to group members for “processing," such as filing fraudulent tax returns.
How to Stay Protected Against W2 Attacks
Malware is rarely used in W2 cons simply because most conventional email security controls can spot malicious code, and attackers are able to make plenty of money without it.
Instead, impersonation is the name of the game. It should be set in stone that the CEO or other executive should never ask for W2s for the entire company, as most of that information is handled within the appropriate departments. Phishing simulation training and education on this form of fraud with payroll and HR departments is key, as they are the ones who are targeted.
Finally, identity-based phishing defenses should be deployed to block these attacks from ever reaching targets in the first place. Organizations should source solutions that leverage real-time threat intelligence from sender behavioral and telemetric data from trillions of emails in order to recognize and reject the highest percentage of incoming attacks possible.
Dealing with the challenges that come with a dangerous pandemic is bad enough without having to fend off phishing strikes, W2 scams, and other advanced email threats.
To learn more on BEC scams and other email threats, read the latest Email Fraud and Identity Deception Trends report from Agari.