Business email compromise (BEC) has become the predominant cyber threat businesses face today. These basic social engineering scams are having a huge impact, to the tune of more than $700 million every month. To make matters worse, the recently-released Internet Crime Report from the FBI’s Internet Crime Complaint Center shows that BEC isn’t going away any time soon, as losses from BEC attacks grew another 37% in 2019 and accounted for more than 40% of all cybercrime losses last year.
Today, we released our latest threat actor dossier on a BEC group we have been tracking for almost a year, which we have named Exaggerated Lion. This report shows how cybercriminal groups are continually adapting and developing new and innovative tactics to increase the effectiveness of their crimes.
Exaggerated Lion is an African cybercriminal organization that has been active since at least 2013. Since April 2019, we have conducted more than 200 active defense engagements against Exaggerated Lion actors. Our visibility into Exaggerated Lion’s operations as a result of these engagements has given us an in-depth look at how their BEC attacks unfold and have evolved over time.
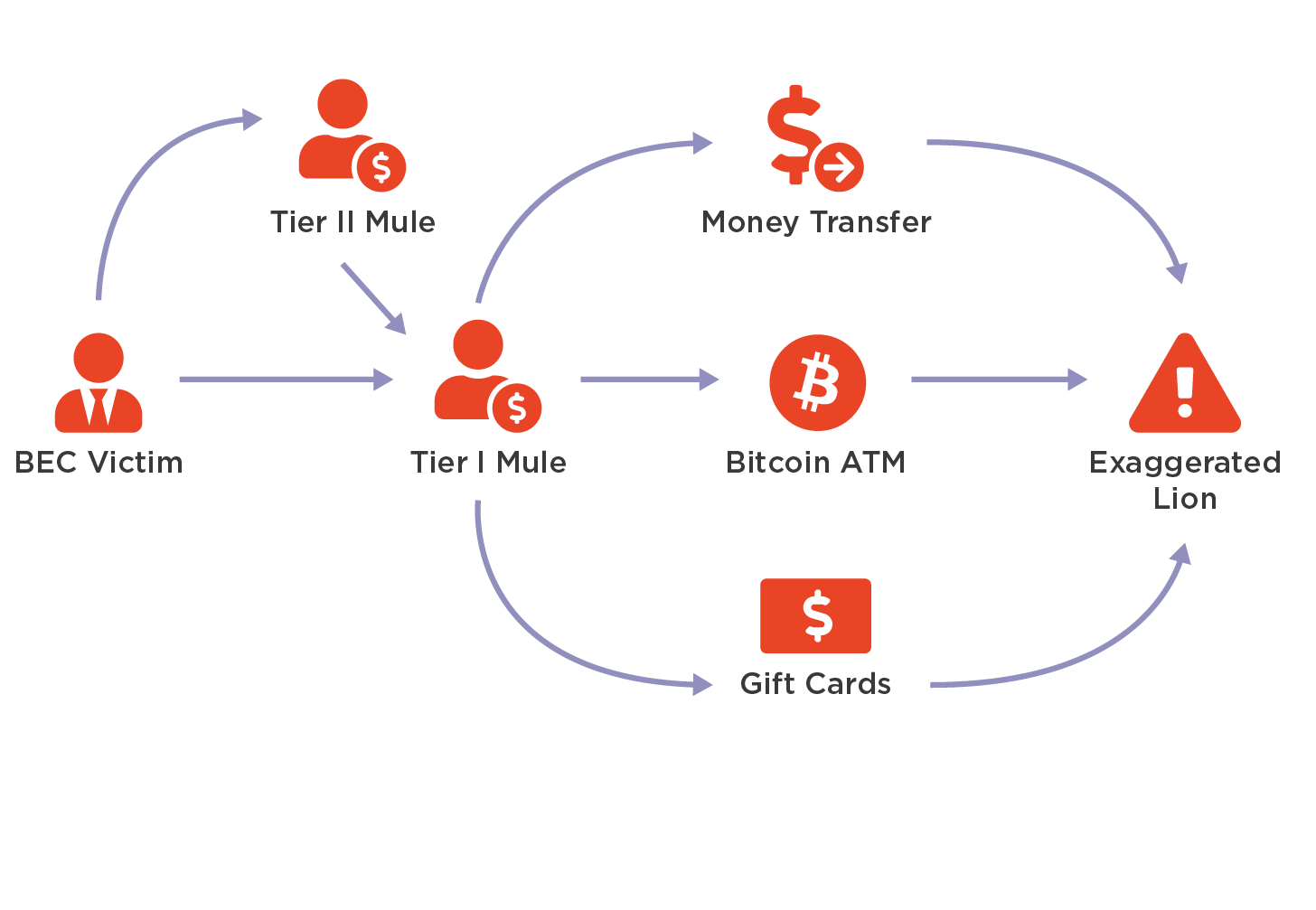
Comprised of actors in Nigeria, Ghana, and Kenya, Exaggerated Lion built a prolific check fraud operation before evolving to BEC attacks starting in mid-2017. One of the most intriguing aspects of Exaggerated Lion’s BEC attacks is their clear preference to use physical checks as a cash out method rather than wire payments, which makes them unique in the BEC threat landscape.
The group’s history of check fraud and romance scams has resulted in a vast network of check mules across the United States. Over the course of our research into Exaggerated Lion, we have uncovered the identities and locations of 28 check mules, including seven “Tier 1” mules who are long-standing romance scam victims that are trusted with large sums of money and who interact more extensively with the main Exaggerated Lion actors.
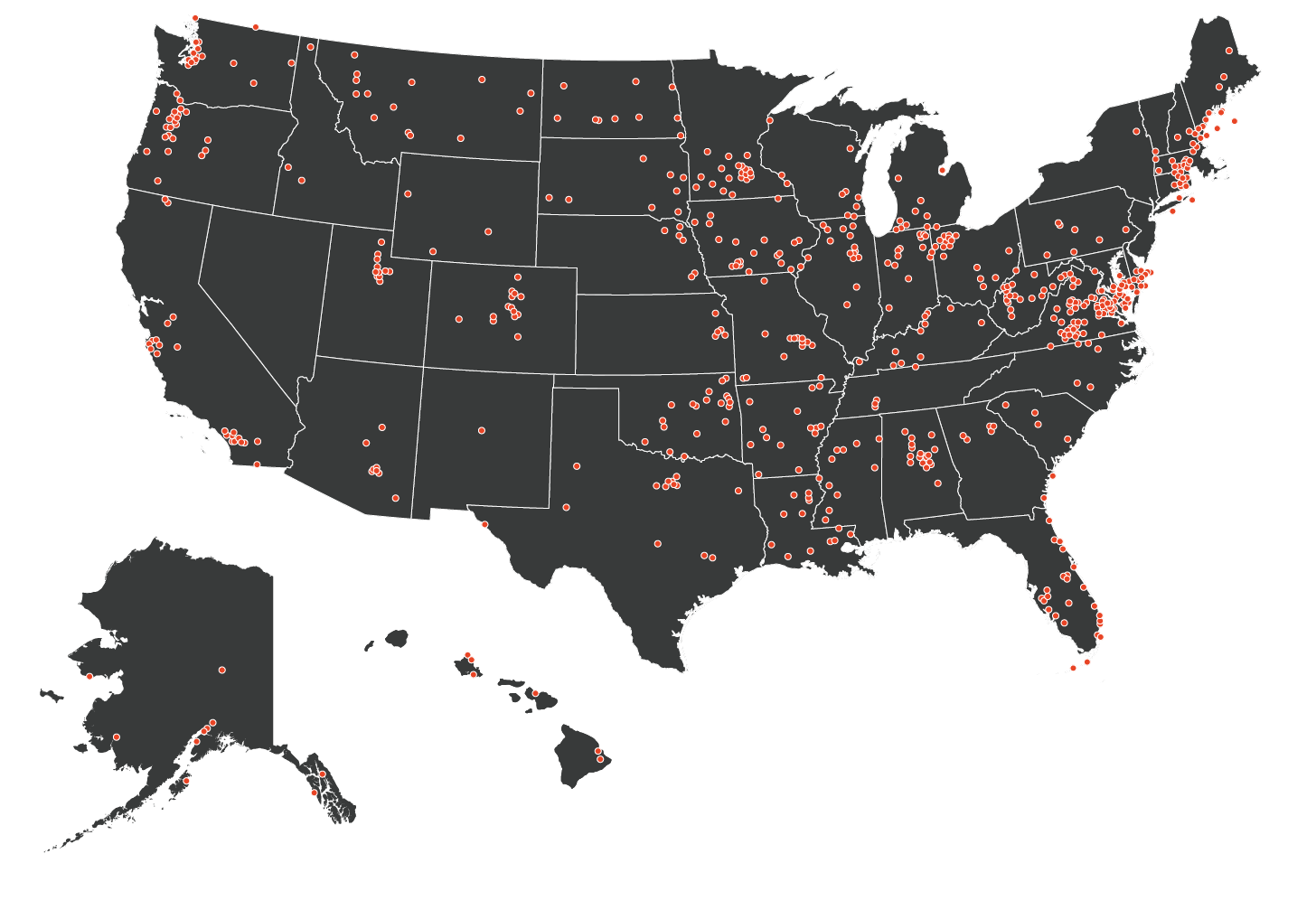
During our research, we identified more than 3,000 individuals employed by more than 2,100 companies that had been targeted by Exaggerated Lion BEC campaigns between April 2019 and August 2019. All of these targets were located in the United States, in 49 of 50 states and the District of Columbia, an indication of Exaggerated Lion’s square focus on American targets.
As our engagements with Exaggerated Lion continued, the group evolved their tactics and started using fake invoices and W-9s to inject a sense of authenticity into their attacks. The invoices were created using an easily accessible free invoice generator and the W-9 forms were obtained from the Internal Revenue Service’s public website. Since these documents are commonly used in legitimate business transactions, including them gives Exaggerated Lion’s attacks a better chance of succeeding without any questions being asked.
Exaggerated Lion’s M.O. has remained remarkably consistent over the years. They use very long domain names hosted on G Suite containing words that give the appearance that an email was sent from secure infrastructure. Our research has uncovered more than 1,400 domains used by Exaggerated Lion since July 2017 that have been used to launch BEC campaigns. Domains registered by Exaggerated Lion actors comprise more than 10% of all .MANAGEMENT domains that have ever been created and nearly 75% of all .MANAGEMENT domains that have ever been registered with Google.
To protect against threats like Exaggerated Lion, organizations first need to understand and accept the state of today’s cyber threat landscape. Most email-based threats today, like BEC attacks, are very simple social engineering attacks that are technically unsophisticated. To effectively protect against these threats, companies need to make sure they have defenses in place that are equipped to detect identity deception attacks that traditional inbound filters are not accustomed to handling. Additionally, organizations should have good internal processes in place, so payment requests, regardless of source, are verified before they are processed.
Business Email Compromise (BEC) and Google Workspace: How the Exaggerated Lion Cybercrime Group Cashes Out
Posted on February 19, 2020