Business Email Compromise (BEC) was solely responsible for over 40% of the total cybercrime losses in 2019, at least according to the latest FBI IC3 report.
The FBI’s Internet Crime Complaint Center (IC3) has released its latest Internet Crime Report with data on cybercrime impact in 2019. Corporate data breaches, which lead to leaked databases, documents, and bad press coverage for the company, are some of the scariest times an organization can face. While this can be embarrassing, data breaches aren't causing the most damage, as they rank at #24 by victim count. When we look at the confirmed losses reported to the FBI, what’s really causing the most damage to organizations?
Two other threats, malware / scareware and ransomware rank #22 and #23 on our list of confirmed victims. By volume, attacks involving spoofing and BEC come in at #5 and #6 on the list, with BEC having 13 times more victims than reported corporate data breaches.
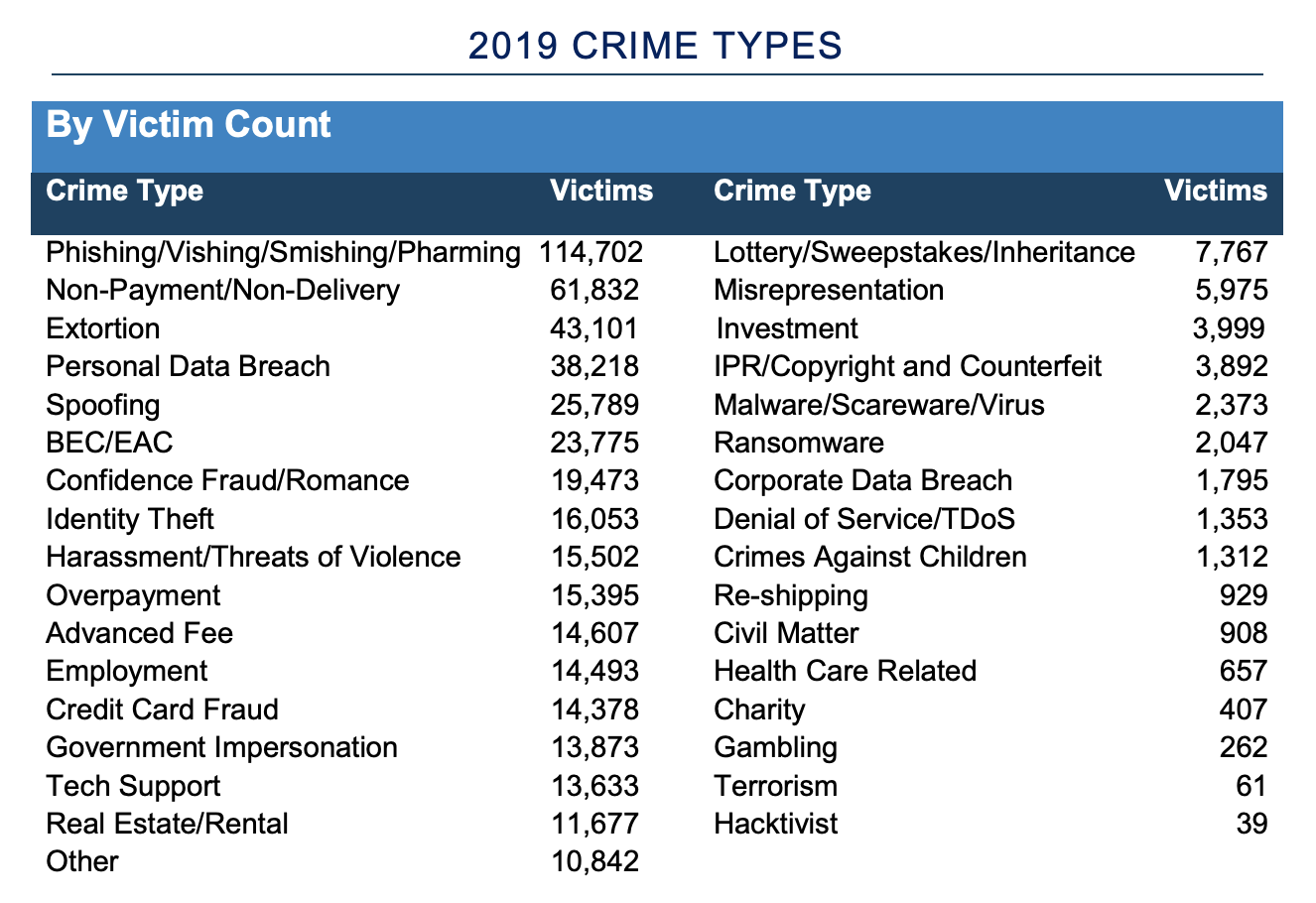
Looking at the metrics, is some super sophisticated APT from China or North Korea causing the most damage, or is a "simpler" threat causing more of a problem? With all the hype around the technological sophistication of cybercriminals, you might be surprised that crimes committed by BEC actors are responsible for over 70% of ALL cyber crime reported to IC3. And that’s just the tip of the iceberg.
Many security vendors tout their solutions as a way to mitigate malware, scareware, viruses, and ransomware, all trying to prevent corporate data breaches. Accepting all vendor claims and assuming that the volume is somewhat representative of the attacks that happen, you would have successfully mitigated 26% of the attacks against your organization by acquiring these solutions.
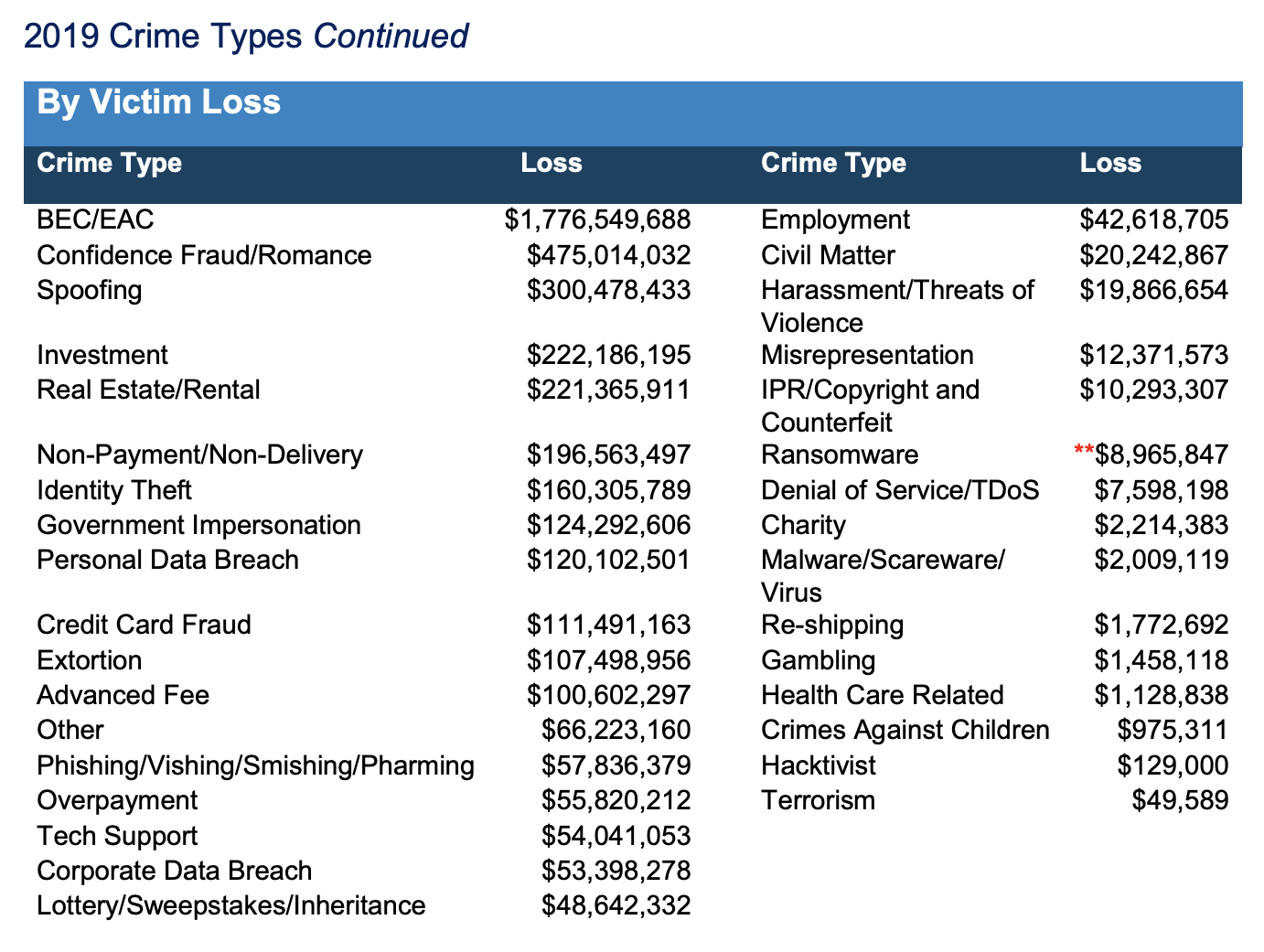
Looking at the actual losses tied to cyber incidents paints a much worse picture. Corporate data breaches move up the list to #17, with BEC ranking in as the #1 threat by reported losses, causing over 33x the financial damages of corporate data breaches. Let that sink in for a while.
Incident responders typically use the cost per incident as a rationale for focusing on malware attacks and data breaches; however, that calculation is becoming quite dated, based on the actual data of confirmed victim losses. The average cost per BEC incident is $74,723.44, with the average cost of each corporate data breach being $29,748.34. Sure, maybe not all corporate data breaches make the news, but likewise a lot of BEC attacks don’t, either. And, while we’re at it, the average romance scam victim loses an average of $24,393.47 per incident, who are frequently recruited as money mules for BEC actors.
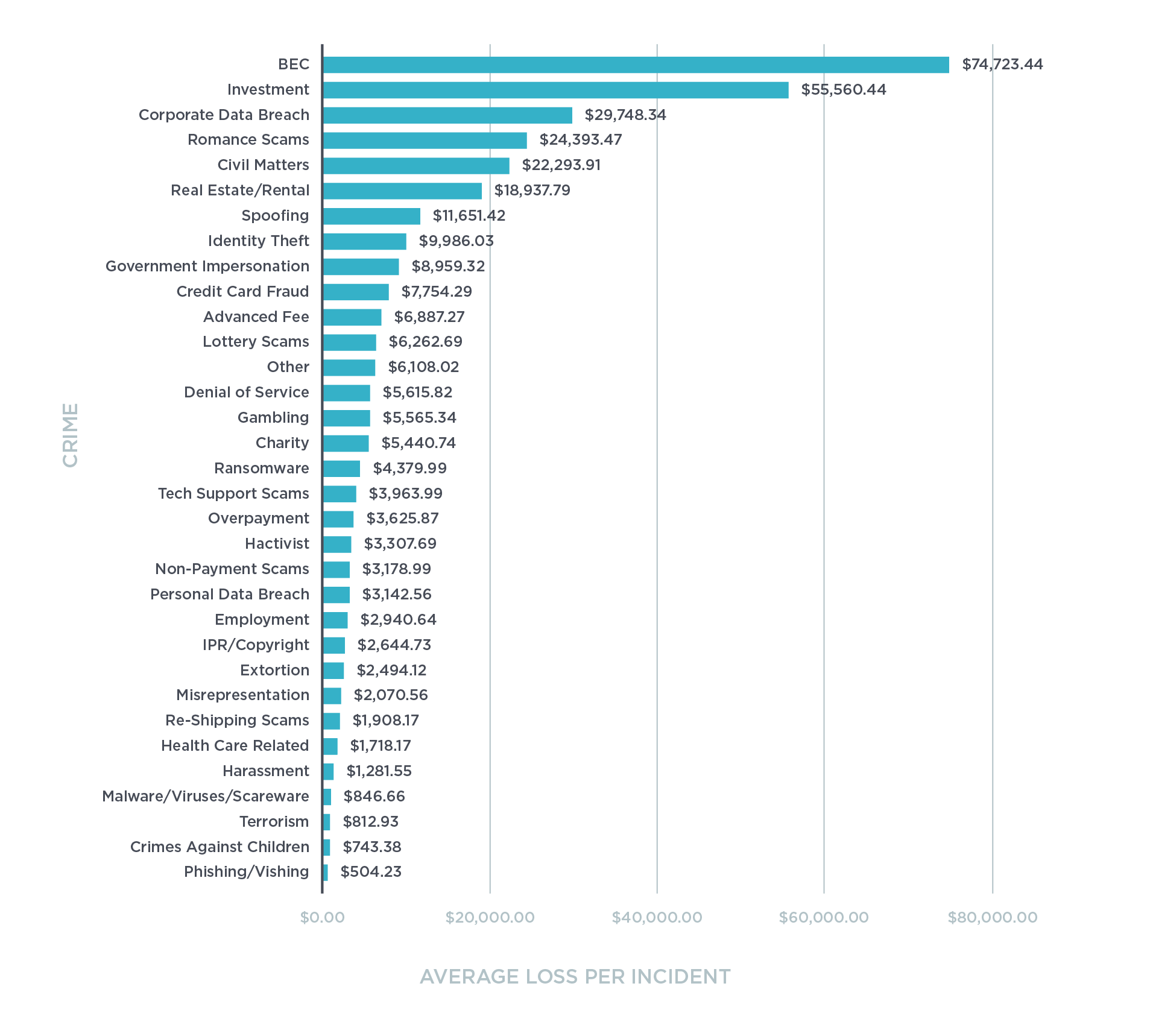
By graphing the confirmed losses, we can start to see where our efforts should be focused in order to protect our organizations against the ever-changing threat landscape.
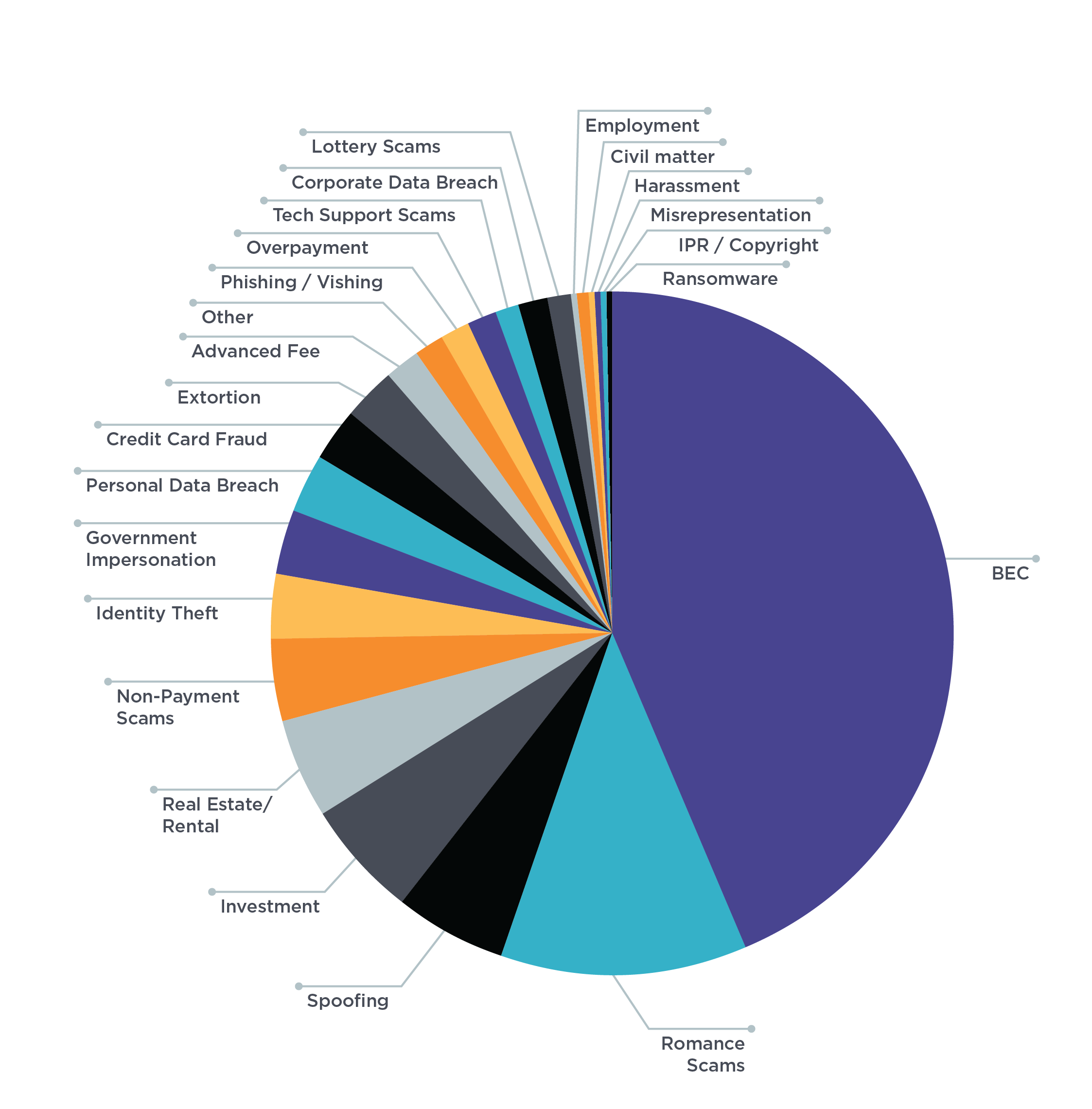
Based on our research into BEC gangs such as Scattered Canary, we know that BEC overlaps with other types of cyber crime, including romance scams, investment fraud, check fraud, and real estate scams, just to name a few. By highlighting the other crimes typically committed by BEC actors, it really starts to put into perspective where the most significant problems actually exist.
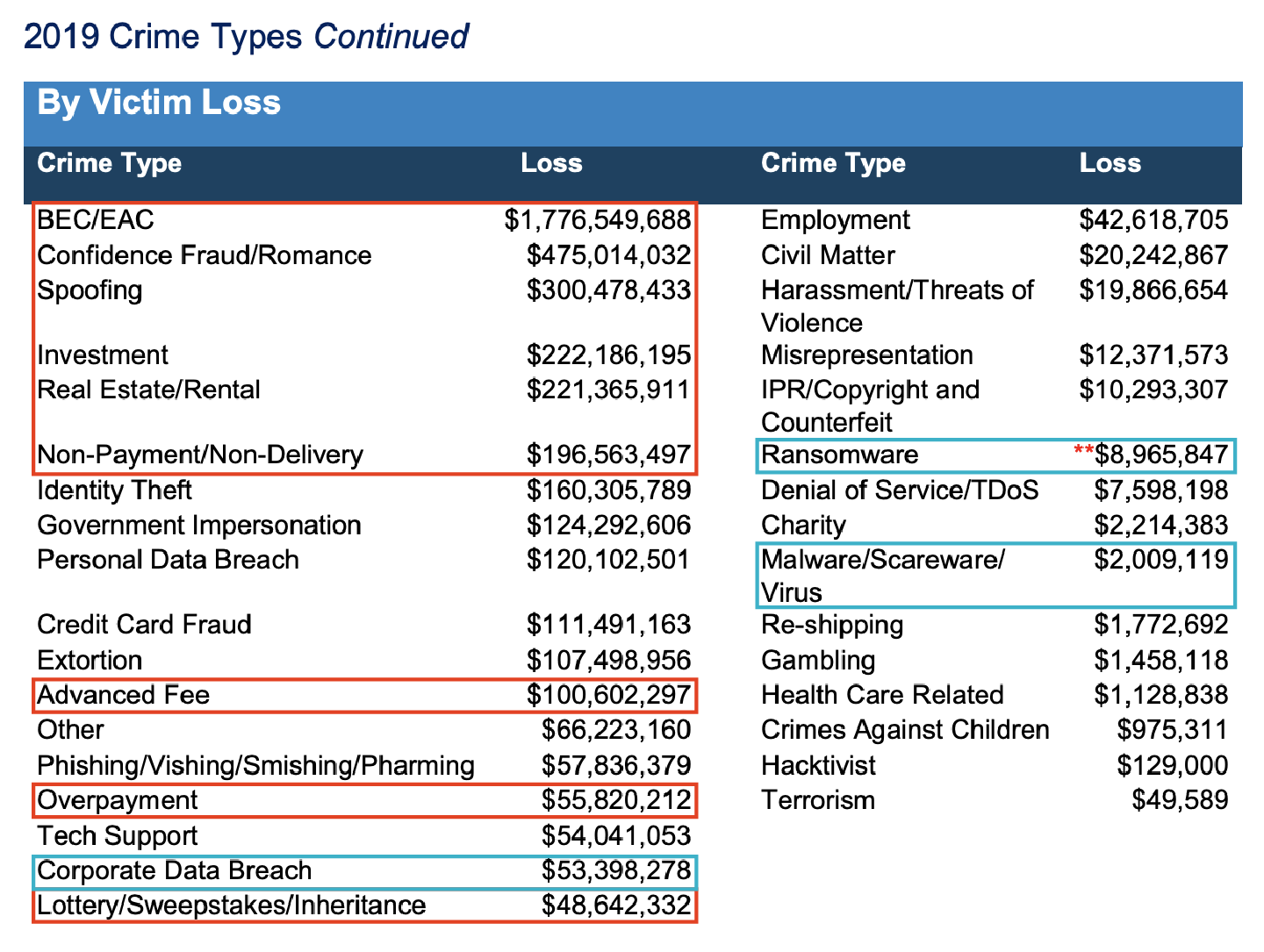
By comparing fraud committed by BEC actors to corporate data breaches and malware, it becomes clear that focusing on BEC and other spoofing attacks makes the most sense, because this actually represents a much higher loss -- about 64 times as much!
Look, I’m not saying that we have to completely do away with hunting APT threats because they’re still just that...threats. But when BEC related crimes account for over 64x the actual damages of corporate data breaches, maybe it’s time for your CISO to say “Oh hey, maybe we should implement DMARC.”
Back to the basics checklist:
- Is DMARC enabled and configured correctly?
- Are you regularly patching systems?
- Do you have systems in place to detect phishing and BEC?
- Are you performing regular employee phishing simulation and training?
- Is the SOC team equipped with tools to rapidly remediate threats that activate post-delivery?
- Have business and especially payment processes been hardened against fraud?
- Have HR and payroll processes been hardened against W2 and payroll diversion?
- Have processes for handling sensitive and confidential information been hardened against fraud?
- Is 2FA enabled for corporate accounts to prevent ATO attacks?
- If there is a breach, is logging on the endpoints enabled?
If you can answer yes to all of the above, you’ve potentially addressed the 80% problem now leaving you free to focus on the remaining 20%.