Human resources departments are the epitome of task ownership, carefully and efficiently connecting an organization’s needs with that of its employees. Employees in HR are tasked with recruitment, onboarding, and employee relations, and oftentimes handle payroll and benefits. Because of their wide reach, threat actors are now turning their attention to this organizational pipeline as they continue to evolve their employee-to-employee attack vectors.
The Agari Cyber Intelligence Division (ACID) has recently observed a considerable increase in attempts to divert payroll through the use of social engineering techniques. These criminal gangs have invested a great deal of resources into researching and establishing organizational hierarchies, and are undoubtedly looking to secure a return on that investment, even if a previous attempt at business email compromise has proven unsuccessful.
Assuming the identity of the CEO seems to be the preferred tactic for the threat actors, but there is no reason that this type of payroll fraud attack cannot utilize the identity and role of any employee within a company. As the primary aim is to divert a monthly salary payment to a bank account the criminal gang controls, it’s logical they would ideally purport to be those most likely to receive the highest compensation.
Like what happens in most other business email compromise attacks, these adversaries set up a temporary email account and switch the display name to the name of the individual they are attempting to impersonate. Once the fraudulent account has been created, an email is sent to someone within the payroll organization—typically within the finance or human resources departments.
In this initial email, the attacker requests to make a change to their existing payroll direct deposit account details and asks what is required to process the change.

From this point, the threat actor will be thinking on their feet to a certain extent; their main aim is to avoid being directed to any online third-party HR solution that would require access details they do not possess. Knowing this, any attempts to add undue urgency or absolve themselves of the ability to complete the usual process should immediately trigger a red flag. It should also be noted that the threat actors are not phased by being asked to provide a voided check displaying the new accounts details, and have successfully provided these when requested of them.
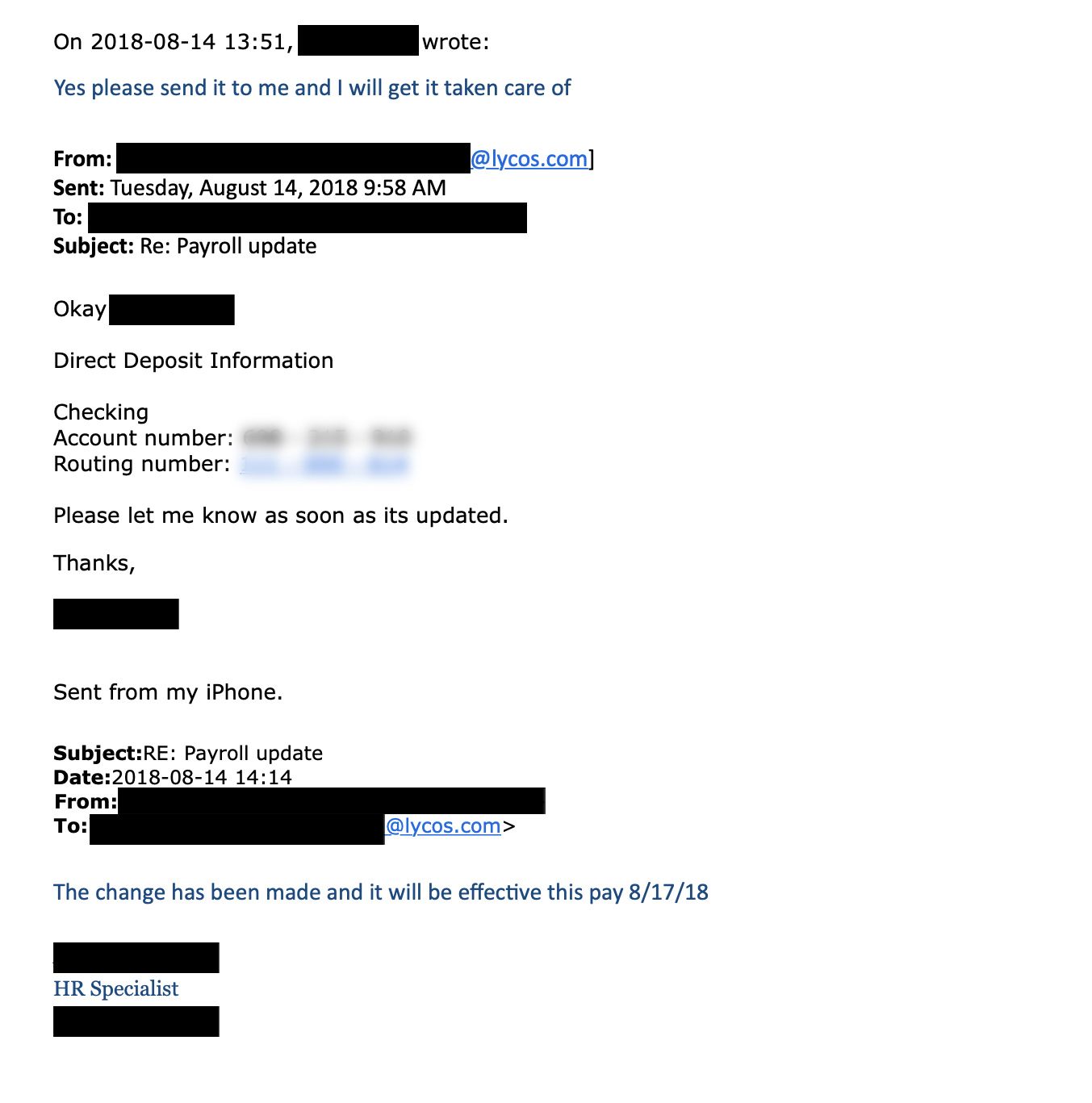
By avoiding third-party systems and asking for help from the human resources employee, the threat actor can control the entire situation and successfully divert pay into the fake account they own. Depending on how the real employee checks their bank account, this scheme can continue for weeks, or even months, before the attack is caught.
Overall, we advise all organizations—large and small—to evaluate their current processes for updating payroll details. If a two-factor online system is not being used, we recommend ensuring an element of human contact is established before completion of the request, in addition to checking that email address is from a legitimate source. As with all email attacks, one can never be too careful.
New Trend Sees BEC Gangs Focus on Executives for Payroll Diversion Scams
Posted on January 14, 2019