As 2020 gets underway, business email compromise (BEC) scams and phishing attacks are expected to get a whole lot worse. But today, a new form of expert-curated BEC intel promises to help organizations stay ahead of emerging attacks like never before possible.
Businesses can use all the help they can get. With more than $8.6 billion lost to BEC and variants such as vendor email compromise (VEC) in just the last year, attacks perpetrated through email grow more sophisticated and costly by the day. Just look at Toyota, which lost $37 million to email schemes in recent months, or Japanese media giant Nikkei, which lost $29 million.
As traditional email security systems have grown adept at sniffing out malware and malicious links, it's clear that email attacks have gone low-tech, high-stealth. By using stolen login credentials to infiltrate legitimate email accounts within a company, or by creating a spoof account using webmail platforms, these cybercriminals engage in email impersonation to defraud companies—producing blistering financial and reputational damage along the way.
At Agari, it's our mission to help businesses tip the scales in this escalating battle against identity deception-based email attacks with our industry-leading solutions. And with our Winter '20 Release, we're helping customers to further fortify their arsenal against phishing and BEC scams with another breakthrough industry first.
Expert-Curated Intel to Protect Against BEC
It may help to get a lay of the land, to understand the power of our latest product update.
Using advanced machine learning and real-time threat intelligence from more than 2 trillion emails annually, Cloud Email Protection has proven itself time and again in real-world deployments by blocking incoming phishing and BEC attacks.
What's more, its continuous detection and response (CD&R) technology leverages crowdsourced reports from top security operations teams to identify email threats that do manage to evade security—and instantly removes them from employee inboxes.
With our Winter '20 Release, we're adding a distinct type of threat intelligence to help neutralize nascent phishing and BEC scams. To accomplish this, we're drawing on data that provides intel drawn from real-world research conducted by the Agari Cyber Intelligence Division, which actively engages with bad actors to understand their methods. This intelligence includes expert-validated information from BEC scams identified through covert engagement with the threat actors behind them. It's the industry's first and only source of expert-curated intel on emergent BEC attacks.
An Unprecedented View into Emerging Threats
Let's look at a few examples the kind of intel provided by the Agari BEC Feed.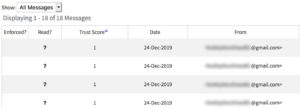
The data above captures information on a BEC attack identified by ACID threat researchers during active engagement with a fraudster. The malicious messages involved in the attack use Display Name Deception to impersonate a specific individual.
In this case, the criminal was spoofing the display name field, claiming to be the CEO (note: the name and email are redacted here). The attack targeted a diverse group of employees. Several additional threat indicators were included in the Continuous Detection and Response event to define its unique characteristics.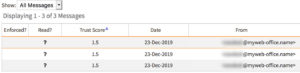
In this second example, a BEC scam uses CEO impersonation to target Accounting department employees. In all cases, threat indicators are reviewed and confirmed by the world-renowned BEC experts on the ACID team, ensuring the legitimacy of otherwise unidentified attacks—informing strategies for defending against them.
A New Level of Protection for a Perilous Year Ahead
Cloud Email Protection customers will immediately benefit from the expert-validated intel provided by Agari BEC Feed—and it's not a moment too soon.
In coming months, the sheer velocity, scale, and sophistication of new email scams could eclipse what has been seen thus far.
After all, BEC and other social engineering-based phishing scams can require little technological expertise. Together with the mass proliferation of breached login credentials, phishing kits, and other cybercriminal tools, this unnerving attack methodology—and its potential profits—will be a clarion call to a growing number of threat actors.
Organizations that deploy effective defenses against social engineering-based email threats will be best positioned to avoid the profound financial and reputational damage these attacks can inflict upon them. And we're proud to provide our customers with a unrivaled new source of expert-validated threat intelligence for achieving that.