Active Phishing Campaigns are coordinated attacks that Fortra has observed bypassing email security gateways and filtering tools. The following analysis includes examples, high-level details, and associated threat indicators.
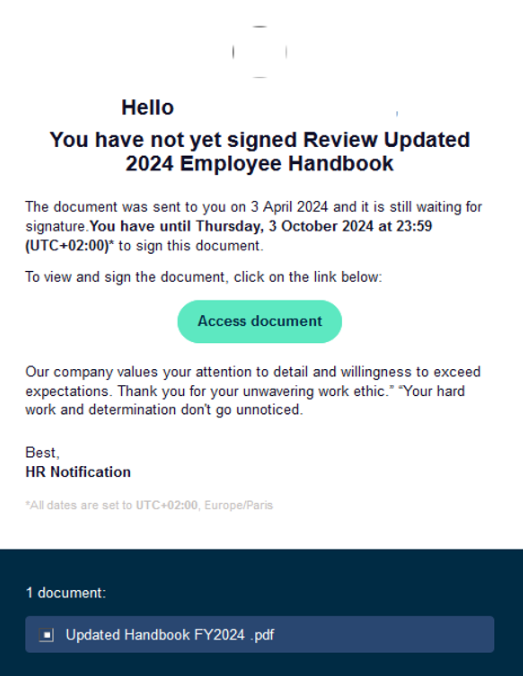
Sample Email Lure
Sender Verification
- Sender’s Email: [email protected]
- Sender’s Name: Yousign for HR Notification
- Registered On: 2018-05-04
- Organization: Yousign
- Analysis: The email appears to be from a legitimate source associated with Yousign. However, the sender is using Yousign to send documents with malicious data entry forms under the disguise of an HR notification. Attackers can leverage these e-signature services to carry out phishing attacks because domains associated with legitimate service providers, such as Yousign, are often not blocked by email filters. As a result, the sender can evade email detection controls and successfully deliver their phishing attacks to the intended targets.
Email Content Analysis

Analysis: The email content impersonates HR departments by urging the recipient to review an updated employee handbook. It includes a signature deadline to pressure and trick the user into clicking the “Access document” button, which lures them into accessing the malicious document.
URL Inspection
URL: The “Access document” button links to hxxps[://]yousign[.]app/signatures/63d95a2c-10ce-4058-ba3d-ea6626646be4?s=1f462e1c46c1fa01b6a400b55a14141394cd62114f4f049c4ea0b2e0dce9cf14aecc175053566d902984be2db7db98bb8a46ab27f8667822158d976127de04e2&r=dbb71db72c01d862f12b18f50d63d99f&source=email&lang=en&magic_link_id=ed0e6c7c-868c-45ad-8310-c4fc0dc8f899&domain_id=e501ed13c0&k=ZxSVjxQ232zri0ZU676wZu8OxP2eAZ0g
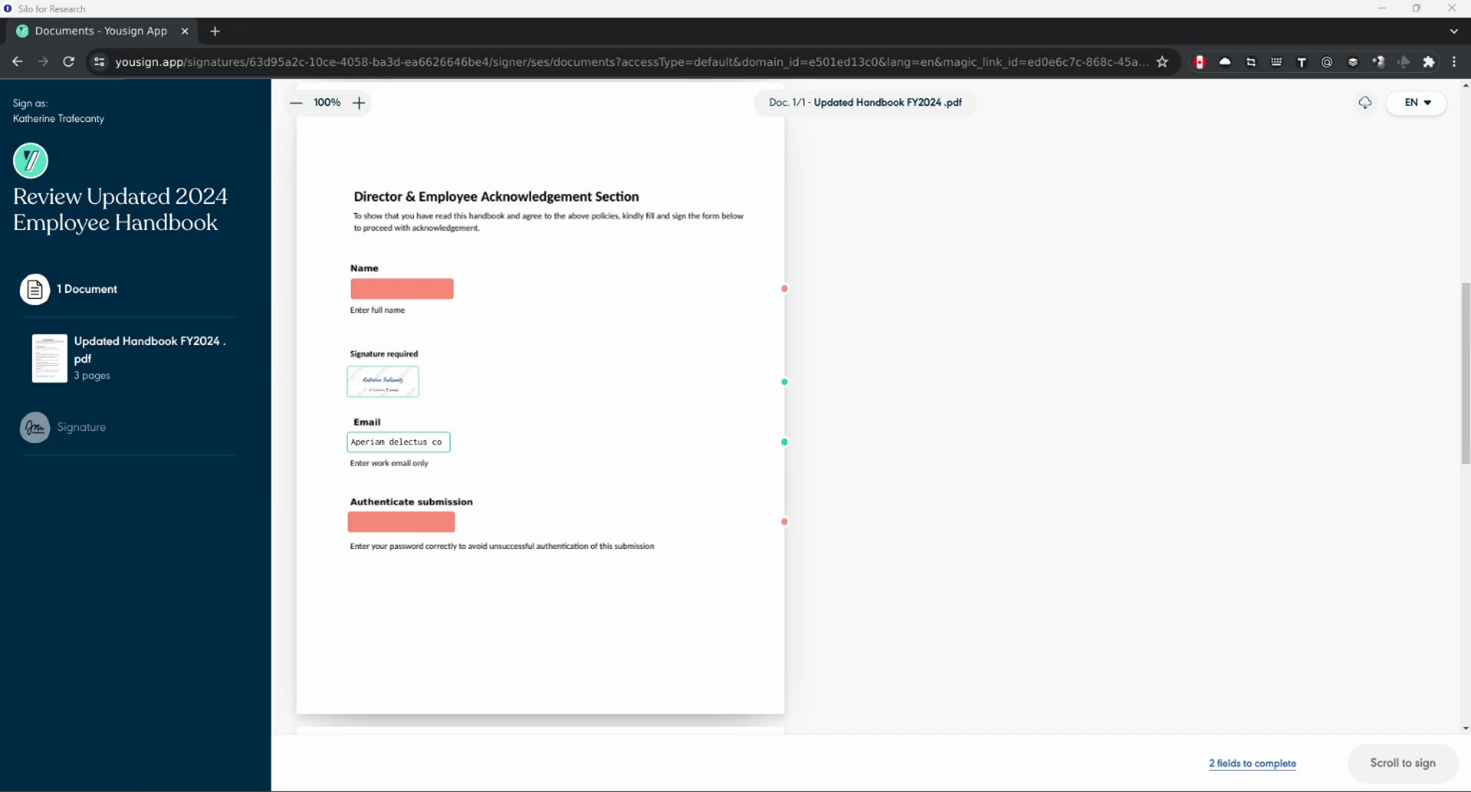
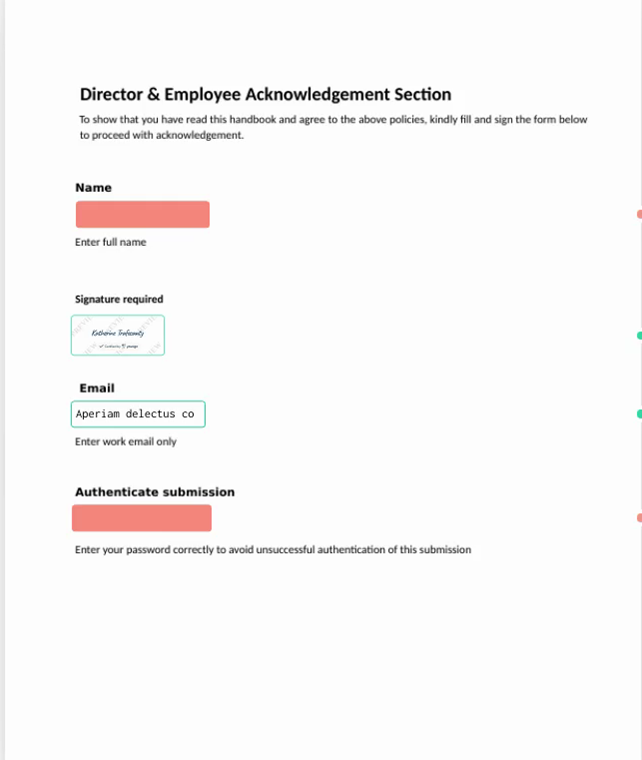
Analysis: The destination URL leads to a legitimate Yousign page containing a document that requires signature. This document is used to harvest the victim’s credentials by requesting the user to enter their work email and password. Given the authenticity of the URL’s destination, it is unlikely that it would be identified as a threat or blocked by web security filters. Threat actors tend to exploit services such as Yousign, particularly those offering free trials or subscriptions, as it enables them to conceal their attack under the service provider’s domain name. Additionally, e-signature services typically generate a unique link for each signature request. These varying links that change with each attack attempt can hinder the identification of specific threat indicators, which is another tactic that the attacker leverages to further evade URL filters.
Threat Indicators
- Sender's Name: Yousign for HR Notification
- Email Subject: You've been invited to sign Review Updated 2024 Employee Handbook