Active Phishing Campaigns are coordinated attacks that Fortra has observed bypassing email security gateways and filtering tools. The following analysis includes examples, high-level details, and associated threat indicators.
Sample Email Lure
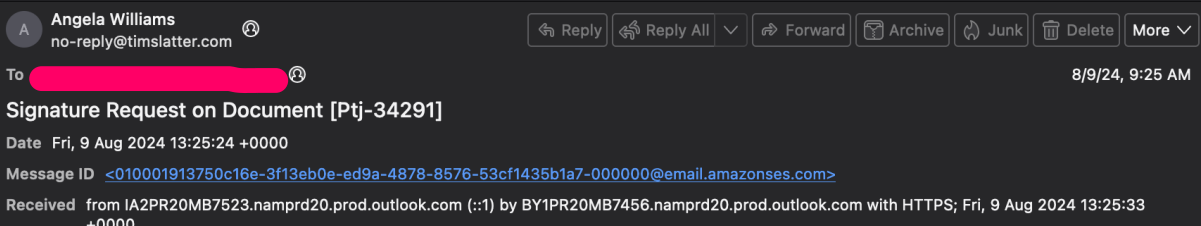
Sender Verification
- Sender’s Email: no-reply@timslatter[.]com
- Sender’s Name: Angela Williams
- Alternate Email Domains: finexstore.com, kosmosrentcar.com and prosoccerstore.co
Analysis: Fortra has observed four different email domains being used in this attack campaign. Each malicious email contains one of these four sender domains and begins with “no-reply@” . The sender typically presents themselves with a random First Name and Last Name, an example of these observed name patterns is Adam Greens <no-reply@prosoccerstor[.]co>. These emails impersonate an organization’s HR department by urging the user to review an employment document, but the sender’s domain name is not associated with the victim’s employer. This discrepancy can serve as a sign of phishing attacks.
Email Content Analysis


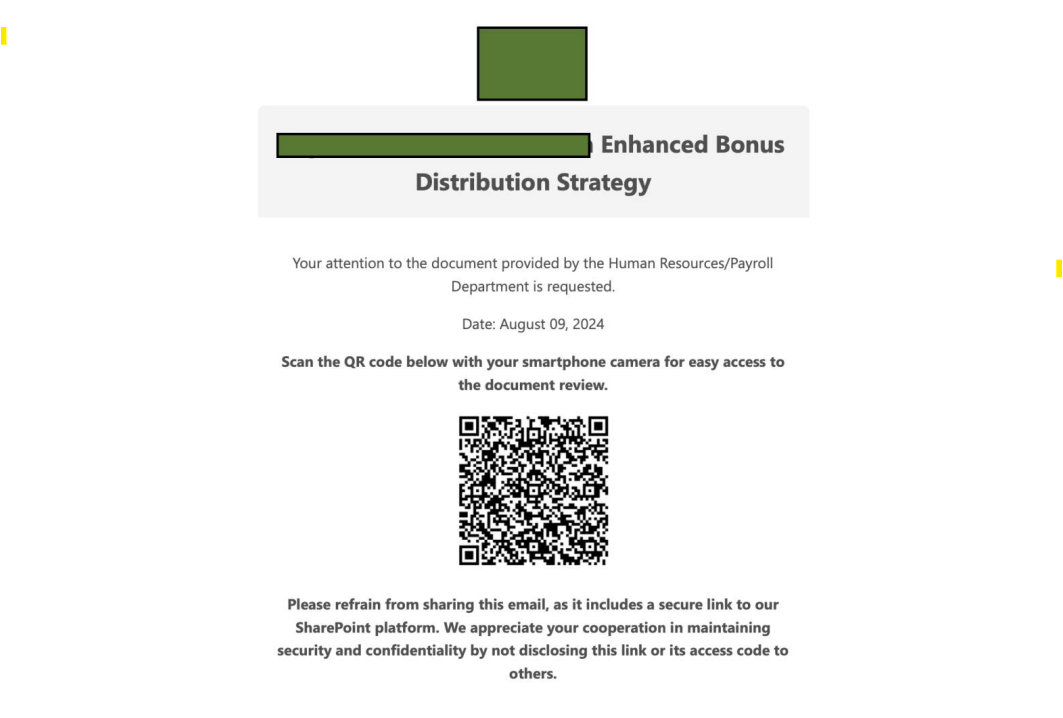
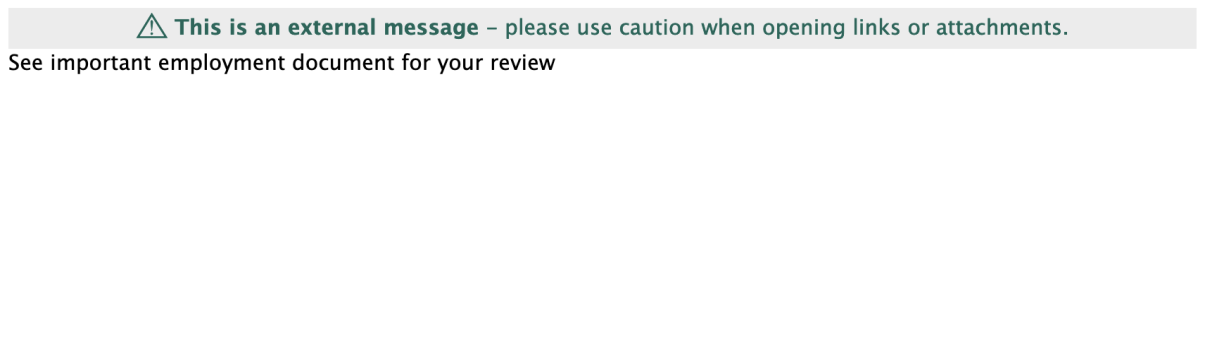
Analysis: In this campaign, the attack begins with a blank email containing only the sentence “See important employment document for your review”. This content is designed to create a sense of urgency and curiosity, prompting the recipient to act quickly and click on the PDF document. All the PDF attachments are named “Secured_Doc-” followed by a reference number that is unique to each email, which is also used in the email’s subject line. When the user opens this document, they are greeted with a message that claims to be from HR, along with a QR code that claims to provide access to an employment document. The attacker impersonates the HR department to establish a sense of authority, increasing the likelihood that the user will be lured into scanning the QR code. Although there are multiple ways to scan a QR code, most users gravitate towards using their smartphones which could be an attempt by the adversary to harvest more data about the victim from their phones. The bottom of the document contains a message that instructs the user not to share this email or the QR code with others, which is a tactic used by the attacker to prevent the victim from consulting colleagues or the IT department who might recognize the attempted social engineering attack. Fortra analyzed the QR codes and discovered that they contain a redirect URL that leads to a phishing landing page where the victim is further social engineered.
URL Inspection
- Redirect URL Domain: donostain.com
- O365 Phishing Domain: dalexglobal.com
- Analysis: After scanning the QR code, the user is redirected to a landing page that contains a fake Microsoft Identity Verification Check.
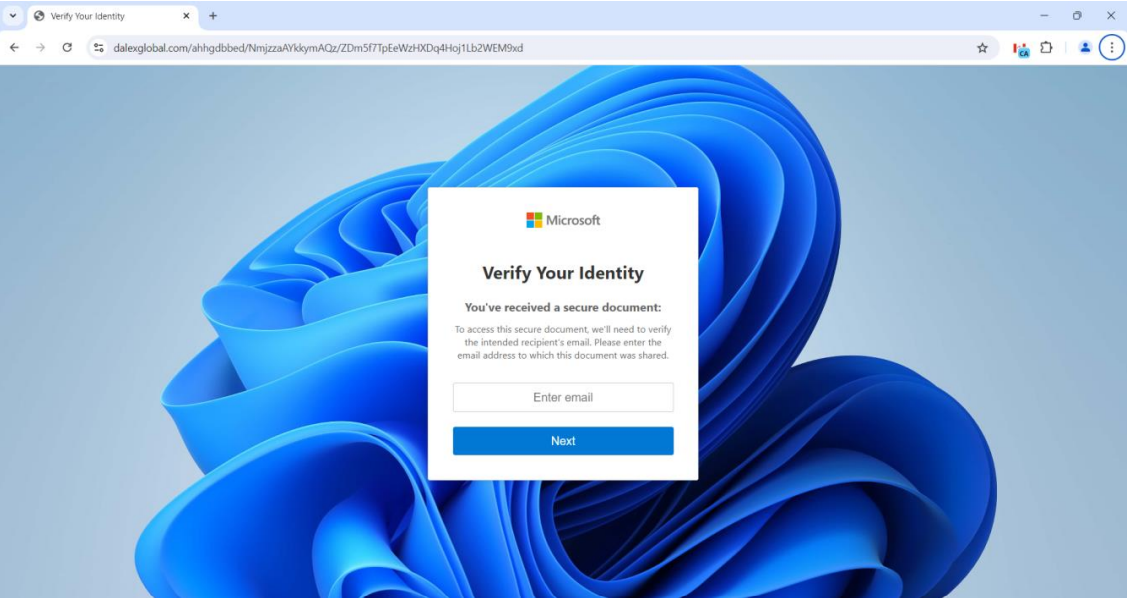
Fortra analyzed the source code of this webpage and discovered that it contains two base64 coded strings. One decoded string is a URL for a site hosting a list with 290,000 emails, and the other leads to an Office365 credential theft page. Fortra also identified that when the user enters their email, the source checks the email address against the pre-compiled list of addresses. If the email is within this list, the user is directed to a fake Microsoft O365 login page designed to harvest their login credentials. The presence of this email list indicates a targeted attack. Additionally, the background of the credential theft page changes dynamically based on the user’s email domain to reflect the organization’s name. This is an attack tactic used by the adversary to increase the page’s perceived authenticity and deceive the user into entering their password.
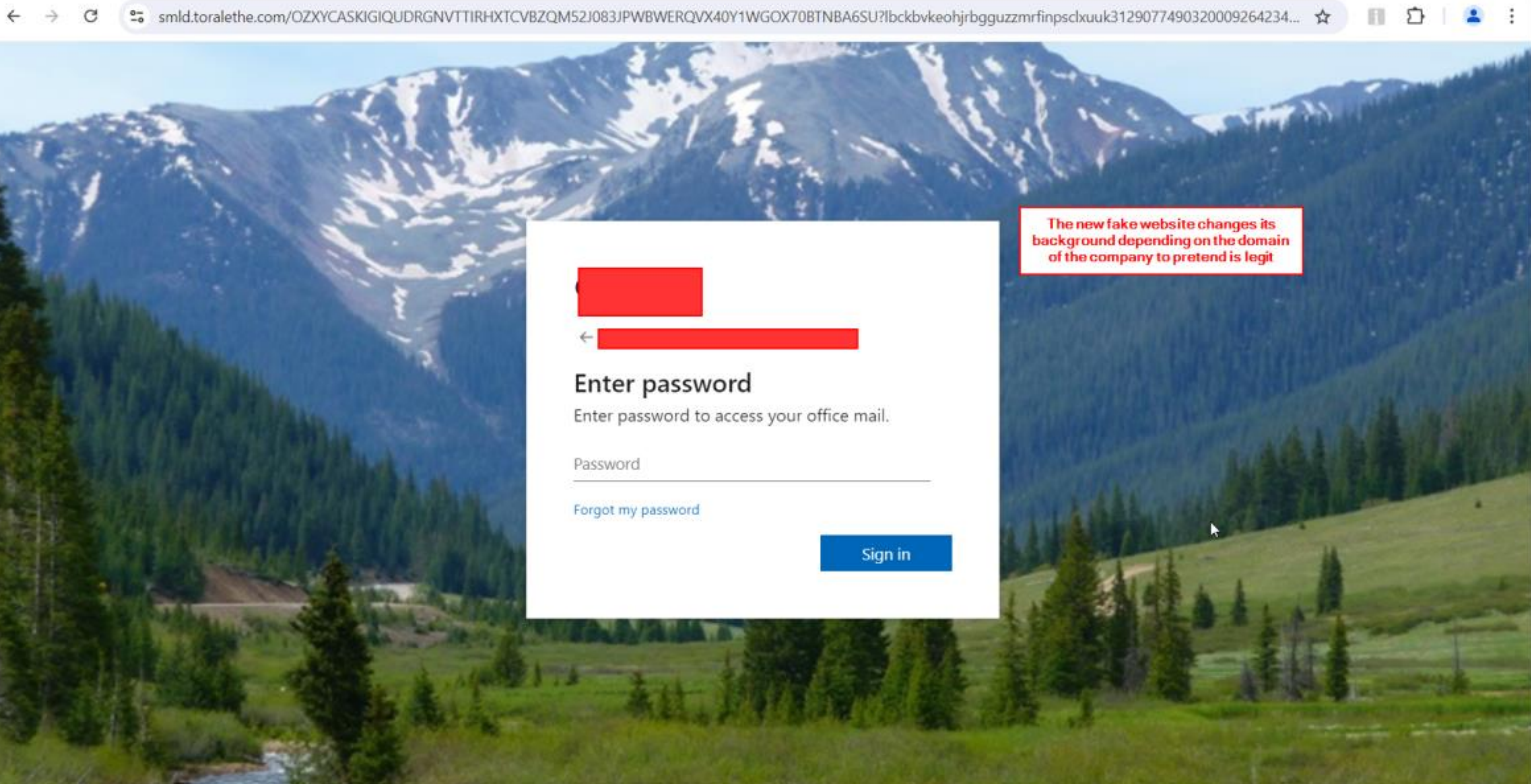
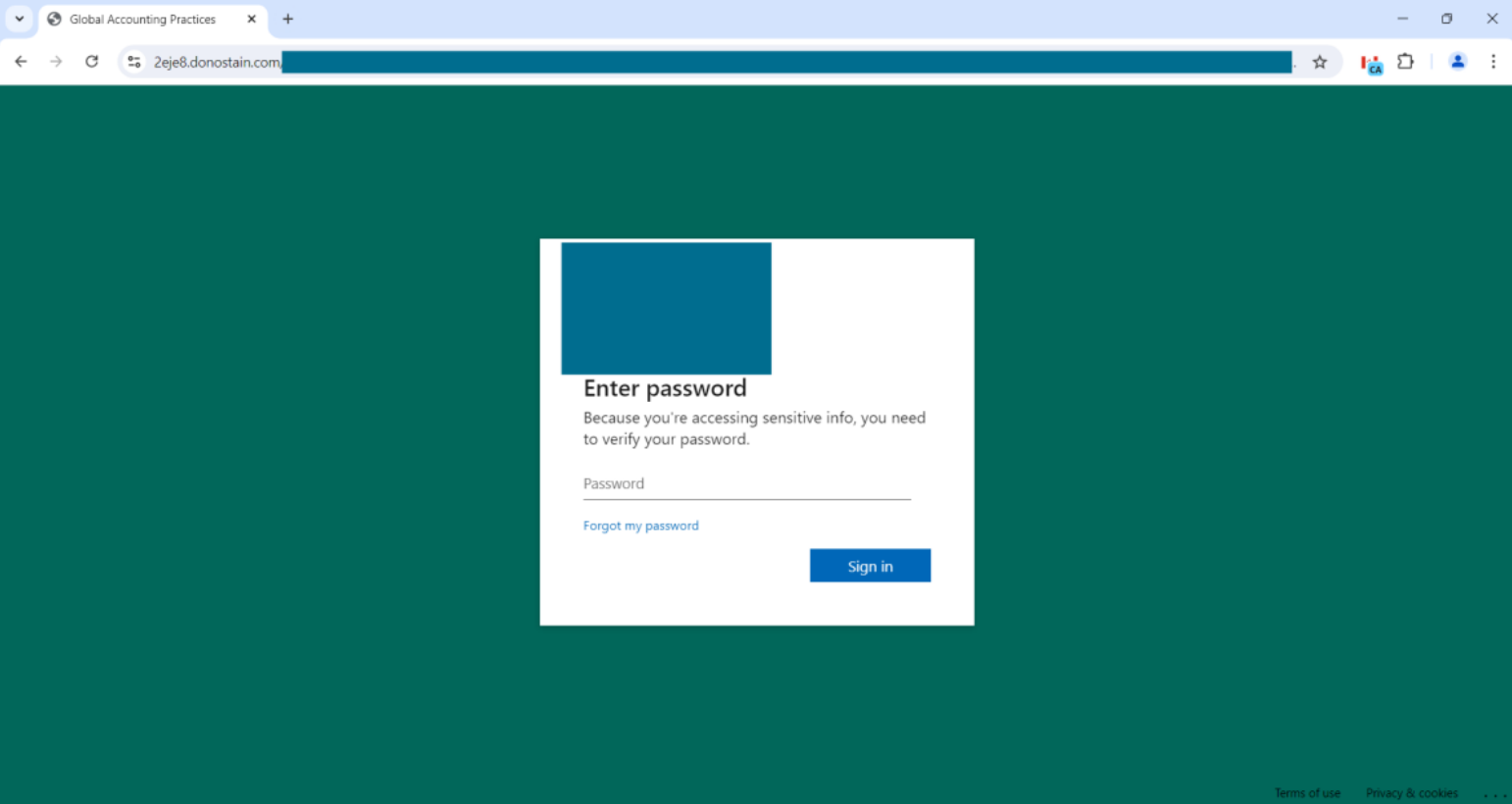
However, if the user enters an email address that is not on the list, the user is then given four attempts to an enter an email before being redirected to a random Wikipedia article. This technique helps the attacker to harvest additional email addresses that may be used in future spear phishing attacks.
Threat Indicators
- Sender's Email: no-reply@timslatter[.]com
- Alternate Sender's Email: no-reply@finexstore[.]com
- Alternate Sender's Email: no-reply@kosmosrentcar[.]com
- Alternate Sender's Email: no-reply@prosoccerstore[.]co
- Email Subject: Confidential Document [Unique Reference Number]
- Alternate Email Subject: Signature Request on Document [Unique Reference Number]
- PDF Attachment's Name: Secured_Doc-[Unique Reference Number]
*The unique reference number refers to a unique number included in every email observed in this campaign, where this number is used by the attacker in both the email subject line and the attachment’s name.
Learn more about how to protect your organization from email threats with Fortra's Email Security solutions.
