Active Phishing Campaigns are coordinated attacks that Fortra has observed bypassing email security gateways and filtering tools. The following analysis includes examples, high-level details, and associated threat indicators. To protect the privacy of Fortra’s clients, the brand targeted in this attack has been anonymized and is generically referred to as “Brand” whenever their name appears in the context of this attack campaign.
Sample Email Lure
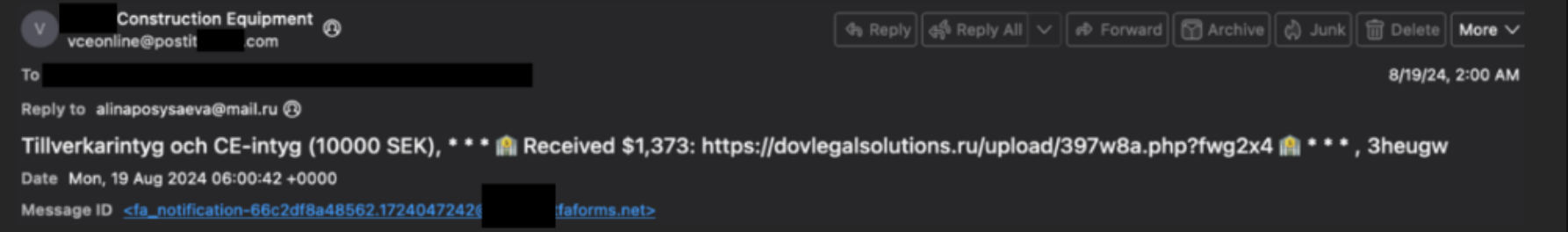
Sender Verification
- Sender’s Email: [email protected][.]com
- Sender’s Name: Brand Construction Equipment
- Reply-To Address: fluffypipichu@yahoo[.]com
- Message-ID: fa_notification [email protected][.]net
- Analysis: The sender of the email is presenting themselves as Brand Construction Equipment, but there is a clear discrepancy between the reply-to address and the sender’s email. In fact, Fortra has observed that a different reply-to address is used for each malicious email. Although the original brand name has been anonymized in this article, the original domain name of the message-id “Brand.tfaforms.net” contained a spelling mistake where certain letters were swapped out in the brand’s name. The spelling mistakes and the mismatched reply-to addresses are multiple signs of a malicious email, as the attacker is spoofing the real sender of the email.
Email Content Analysis

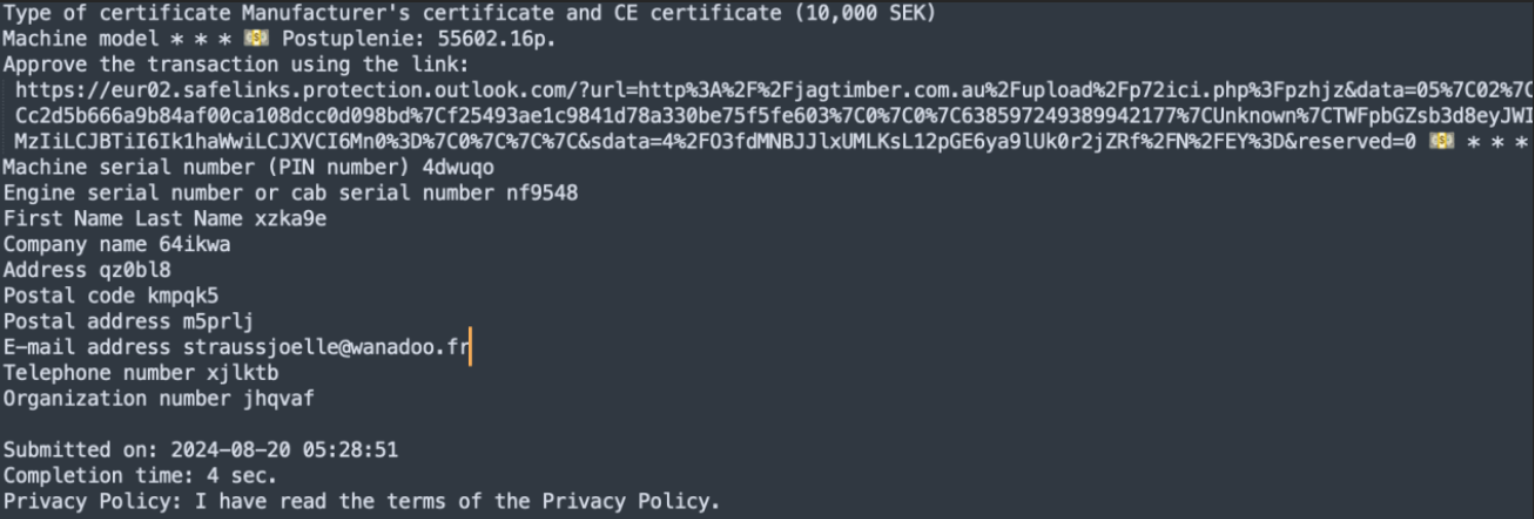
Analysis: The subjects of these emails start with “Tillverkarintyg och CE-intyg (10000 SEK)”, which is Swedish for “Manufacturer certificate and CE certificate”. The subject also contains a link that claims funds are available for the recipient. This social engineering tactic aims to lure the user into clicking the malicious link by leveraging the promise of money to manipulate the target of the attack. The email content of this attack, which is mostly in Swedish and has been translated by Fortra, includes information fields about machine parts and personal identifiable information. Instead of including coherent information within these fields, the attacker utilizes randomly generated six-character strings. This use of incoherent filler email content, along with the absence of legitimate information in the data fields, is a sign of malicious emails.
URL Inspection
- URL: hxxps://dovlegalsolutions.ru/upload/397w8a.php?fwg2x4
- First Redirect: hxxps://reredikos.top
- Second Redirect: hxxps://bitsiop.top
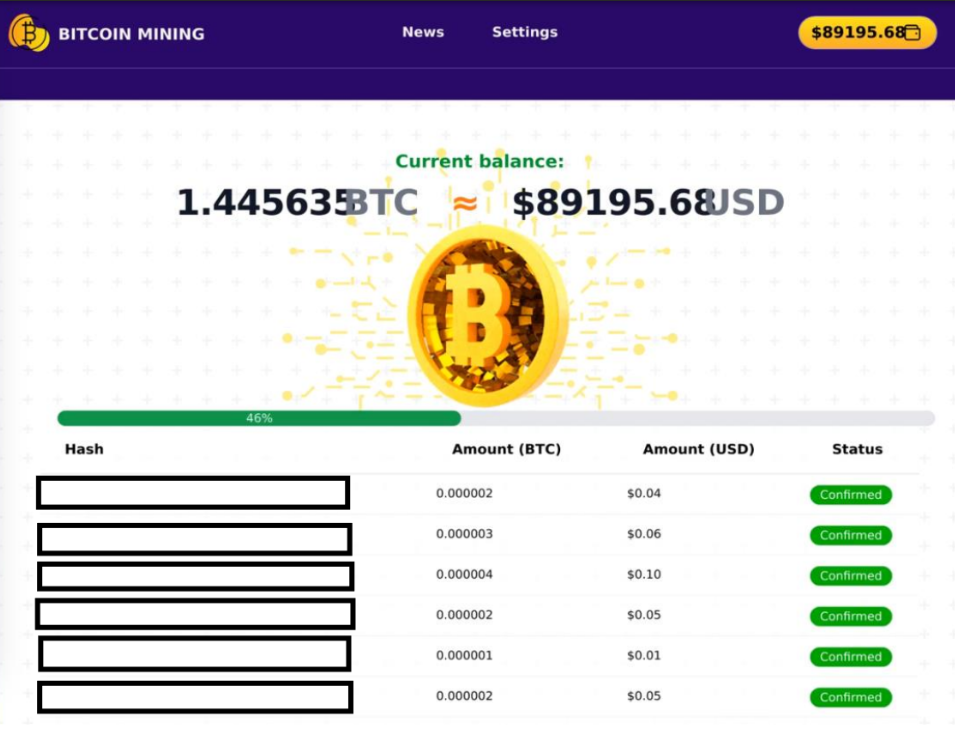
- Analysis: Fortra has identified various variations of the domains used in this attack campaign, including several .com and .ru domains. These domains were registered during the period between 2000 and 2022, raising suspicion of compromise due to their registration patterns. These malicious URLs follow a common pattern that begins with one of three directories (upload/, uploads/ or attachments/) and a PHP file containing a string of 6 random numbers and letters. When the user clicks on the URL, they are redirected twice. The first redirect leads to hxxps://reredikos.top, and then to hxxps://bitsiop.top which is the final webpage containing a bitcoin mining page. The user is repeatedly prompted to allow notifications, and the request persists until accepted. This indicates a potential threat of web hooks that aim to access the user’s browser data. The bitcoin mining page prompts the victim with a fake login screen and proceeds to show different amounts of money coming into a wallet containing over $89,000. The attacker offers this large sum of funds as bait, designed to trick and lure the user into interacting with the attack.
Threat Indicators
- Sender's Name: Brand Construction Equipment
- Sender's Email: [email protected][.]com
- Reply-To Address: fluffypipichu@yahoo[.]com
- Email Subject: Tillverkarintyg och CE-intyg (10000 SEK), *** Received $1,373 hxxps://dovlegalsolutions.ru/upload/397w8a.php?fwg2x4
- Phishing URL: hxxps://dovlegalsolutions.ru/upload/397w8a.php?fwg2x4