If the term “Account Takeover” (ATO) wasn’t part of your cybersecurity vocabulary before, it likely will be soon. According to a new report published by Agari, Account Takeover-based email attacks are on the rise. The research conducted by Agari sites a 126% increase month to month in targeted email attacks that exploit Account Takeover tactics since the beginning of 2018.
To execute an Account Takeover (ATO)-based email attack a cybercriminal first gains access to a trusted email account, then uses this account to launch subsequent email attacks for financial gain or to execute a data breach. ATO-based attacks are particularly dangerous and effective because they originate from email accounts of trusted senders. This has two important ramifications: First, because there is a pre-existing trust relationship with the sender the attack is very likely to succeed. Second, because the attack originates from a legitimate account, they go undetected by traditional security controls.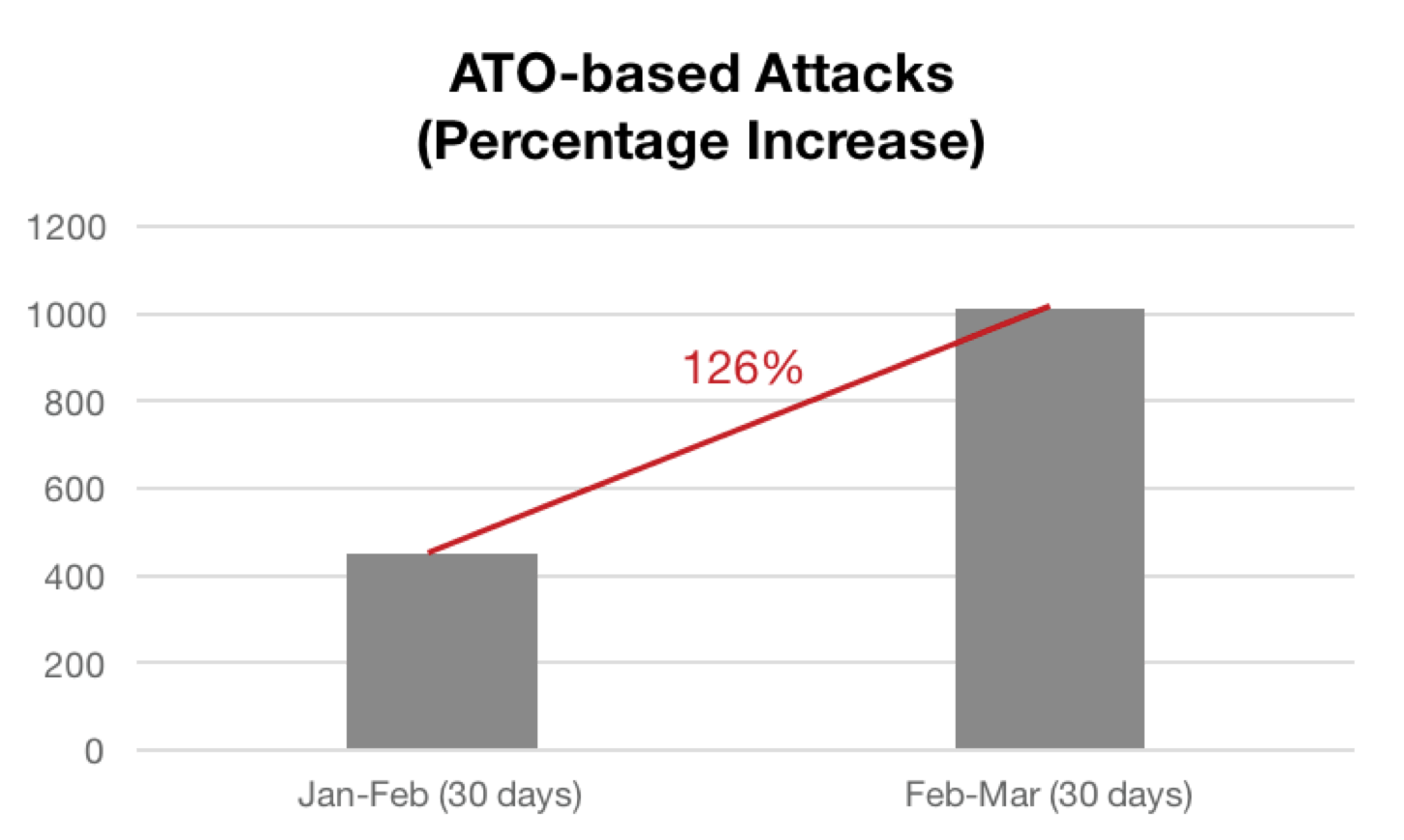
According to the report published by Agari, to execute an ATO attack cyber criminals leverage a compromised account and employ it as a launchpad for a targeted email attack such as Business Email Compromise (BEC). Typically, this involves executing the following five steps:
- Gain account access
- Establish account control
- Conduct internal recon
- Execute a targeted email attack
- Complete mission
STEP ONE: GAIN ACCOUNT ACCESS
Attackers can gain access to a user account by launching a spear phishing or malware based email attack in an attempt to glean a user’s ID and password. Alternatively, the attacker might simply purchase email account credentials from the dark web.
STEP TWO: ESTABLISH ACCOUNT CONTROL
Once an account has been accessed the attacker establishes account control by employing multiple tactics such as creating audit rules that mask his malicious activity, setting up forwarders to silently monitor user communications and changing passwords to maintain password control.
STEP THREE: CONDUCT INTERNAL RECON
Once account control has been established the attacker will patiently conduct internal reconnaissance to determine how the compromised account can be exploited. The attacker may use a set of manual or automated scripts to determine if the compromised account or the user’s credentials provide access to monetizable data or if the victim’s contacts can be exploited to achieve financial fraud, data exfiltration or access to other high-value accounts. Additionally, the attacker may lay dormant, quietly observing email communication between the original account owner and their contacts waiting for an opportune time to hijack the conversation.
STEP FOUR: EXECUTE A TARGETED EMAIL ATTACK
Depending on the type of information gleaned from reconnaissance the attacker will launch an email attack targeting the contact list of the controlled account. This attack could consist of a Business Email Compromise attack to extract funds or a spear phishing campaign aimed at gaining a deeper foothold into the organization. If the attacker determines that assets can be retrieved directly from the account, he will immediately move to step five.
STEP FIVE: COMPLETE MISSION
Depending on the type of targeted email attack employed, the attacker will exfiltrate the sensitive information or funds, or, if user account credentials were requested, repeat the ATO process.
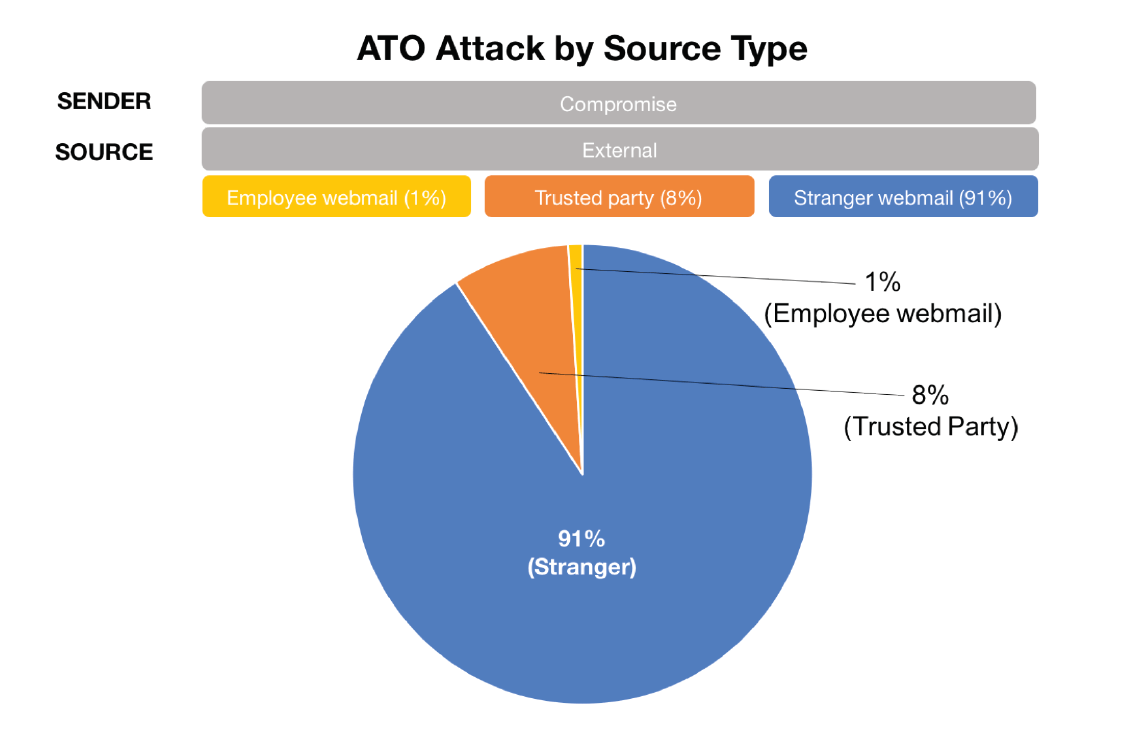
According to the research conducted by Agari, there are four account types used in ATO-based attacks:
- Stranger - attacks using any legitimate email account of individuals unknown to the recipient (strangers) to boost reputation and leverage trusted infrastructure.
- Employee webmail - attacks using personal employee webmail accounts (e.g. Gmail, Yahoo, Hotmail) or accounts of individuals known to the recipient to exploit trust.
- Trusted third parties - attacks using supply chain vendor accounts of individuals known to the recipient to launch spear phishing campaigns.
- Insider business accounts - attacks that use employee corporate accounts of individuals known to the recipient to execute BEC or invoice scams.
ATO attacks by their very nature are notoriously difficult to combat because they utilize legitimate email accounts and therefore have no need to leverage impersonation techniques such as domain spoofing or display name deception to bypass email security controls. At the same time, they are leveraging previously established trust relationships between the original user and their contact, making convincing the contact to give up sensitive data or release funds a significantly easier task.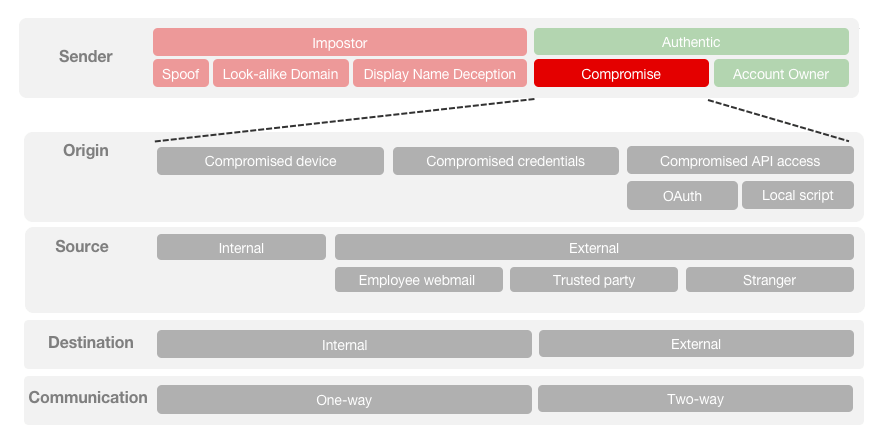
Despite the unique challenges, there are several safeguards that can be implemented using artificial intelligence and machine learning techniques such as identity mapping, behavioral analytics and trust modeling. The Agari research report suggests that the best way to protect against Account Takeover-based email attacks is at the email gateway. Existing security solutions should be evaluated to ensure that they have the ability to:
- Enforce policies to prevent targeted and scattershot phishing attempts intending to steal credentials or compromise the endpoint
- Enforce policies to prevent targeted email attacks launched via a compromised user account, e.g., spear phishing, BEC, or ransomware
- Provide email forensic intelligence that exposes the compromised email account details to help security teams return these accounts to their rightful owners
View the Report