What Is Email Data Loss Prevention (DLP)?
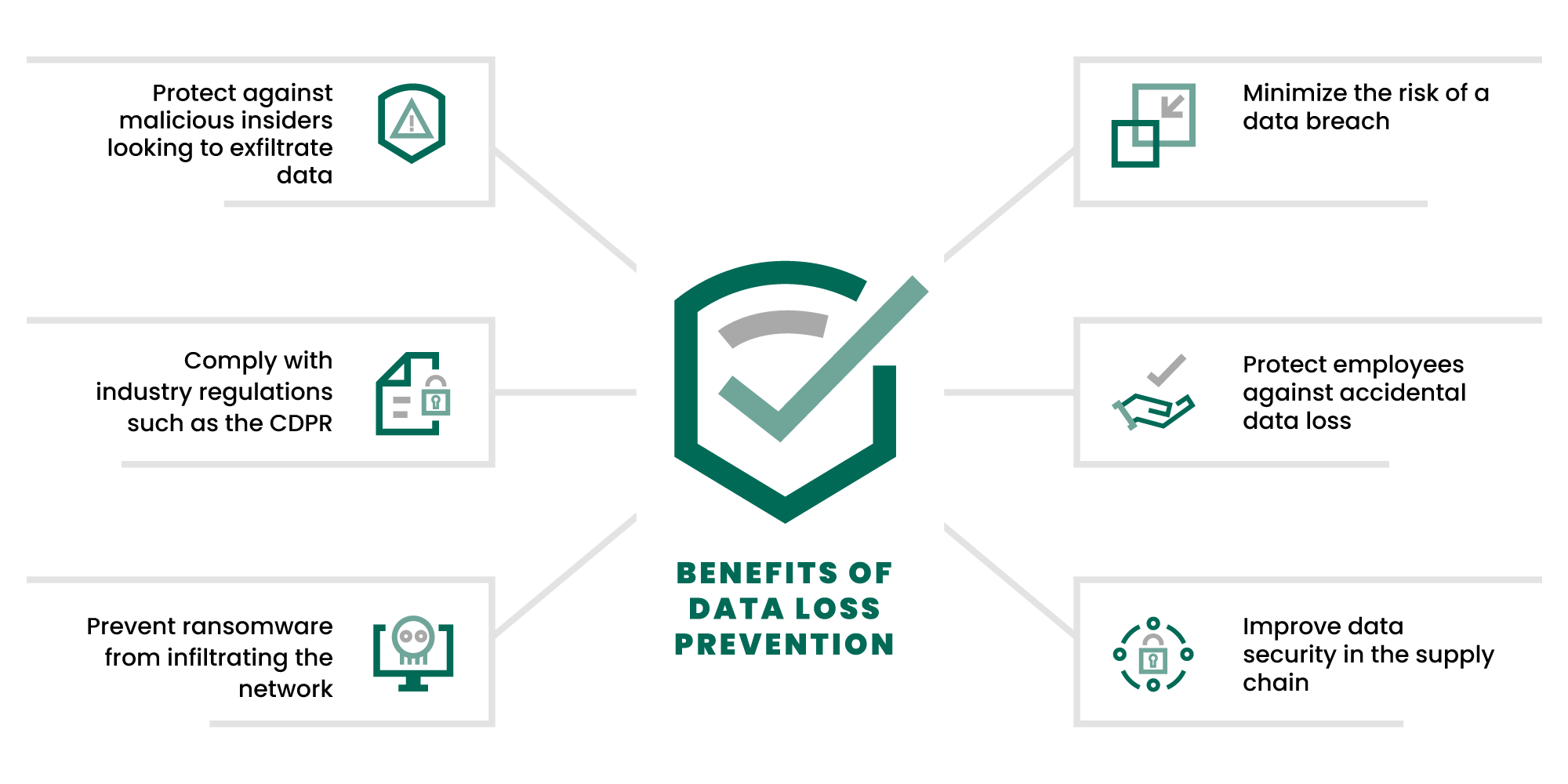
Email Data Loss Prevention solutions are designed to protect sensitive information from accidental or intentional data loss through email. These solutions can detect, monitor, and block any sensitive information from being sent outside the organization's network. Without robust controls, sensitive or valuable data can be leaked accidentally or targeted by malicious actors looking to exfiltrate it for monetary gain. And these threats can come from within the organization (e.g., insider threat) or from the outside in the form of ransomware and other cyberattacks.
To avoid data leakage and exfiltration via email, organizations apply Email Data Loss Prevention (DLP) practices and tools to safeguard their business-critical data, often with a Secure Email Gateway appliance. Email DLP focuses on minimizing the risk to the organization by detecting and preventing unauthorized disclosure via email before the data breach occurs.
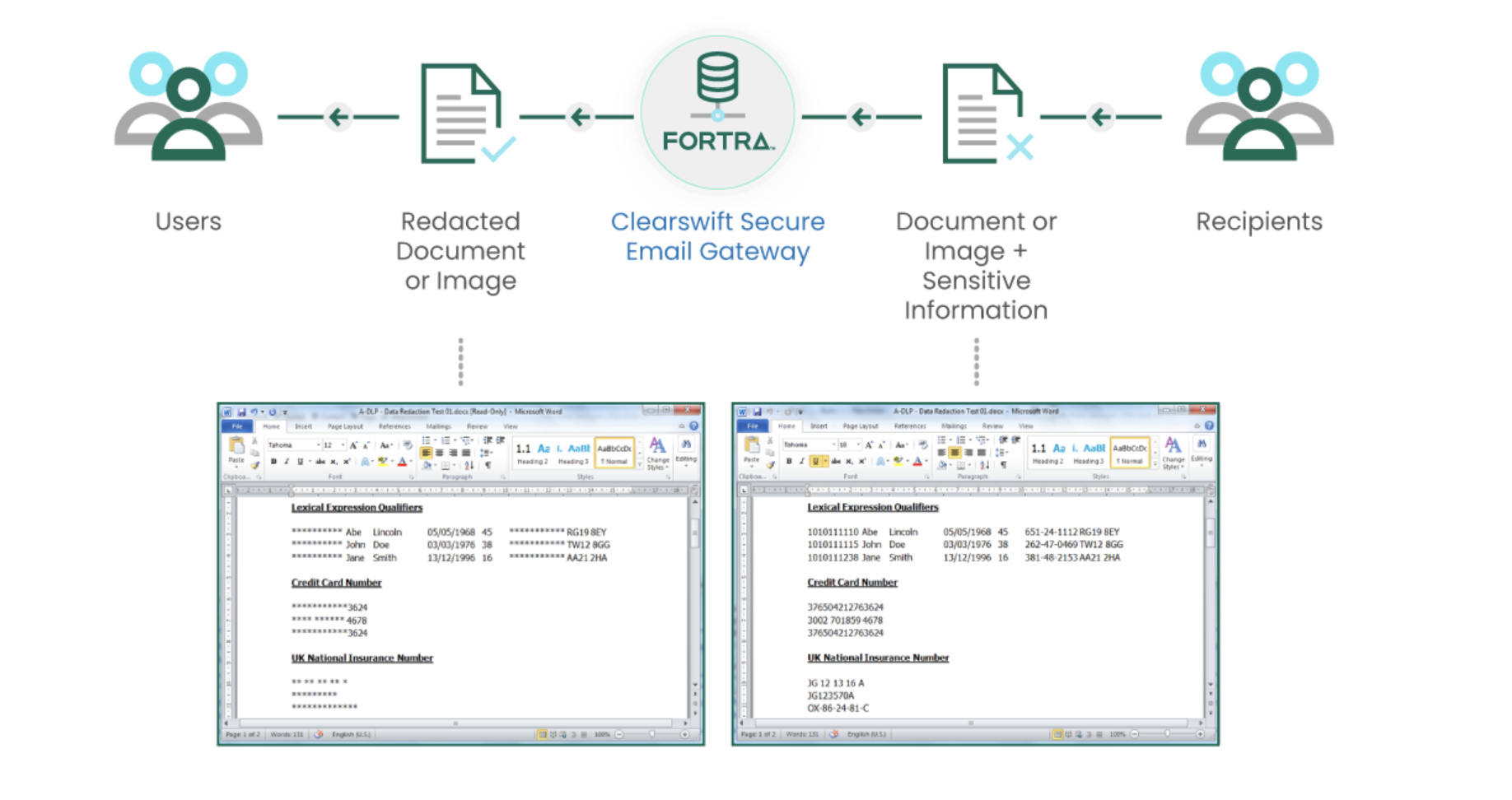
What Is Adaptive Redaction?
Adaptive Redaction technology sets Email Data Loss Prevention apart from other vendors. It occurs during the content inspection process in real time, and deconstructs files down to their constituent parts. Once sensitive or personal information is identified, it automatically;:
- Removes, deletes, or sanitizes the files as per the rules set by the organization.
- Reconstructs them, allowing them to continue without delay.
- Inspection is not limited by zip/encryption, file size, analysis timing delays, or multiple embedded document layers.
What Makes Email DLP Differ from Other Types of DLP?
FLEXIBLE POLICY DESIGN
UNIQUE ADAPTIVE FEATURES
MINIMIZES FALSE POSITIVES
CONTINUOUSLY REMEDIATES
Dig deeper into our Email Data Loss Prevention solution
Enhancing Data Loss Prevention in Microsoft 365
Microsoft 365 (formerly Office 365) is fast becoming the collaboration tool of choice for many corporations. Leveraging the cloud, it allows professionals to create and communicate with ease. Microsoft 365 offers multiple tiers of capability, including provisions for data loss prevention – but are these features comprehensive enough to secure data to satisfy the strictest regulatory requirements?
Adaptive DLP works alongside Microsoft 365 deployments to make the most of the cloud-centric infrastructure, but with zero compromise on security. You'll benefit from greater DLP controls, protection from incoming cyber threats, and more flexibility when implementing policies. as well as a reduced total cost of ownership.
Fortra's Email Data Loss Prevention solution fortifies Microsoft 365 for comprehensive threat protection
READ THE GUIDE
Additional Fortra Solutions for Data Loss Prevention
If you need to better see and protect critical data and IP, Fortra offers additional market-leading endpoint data loss prevention to complement our email security solutions.
Endpoint DLP
The most robust coverage and control for Windows, macOS, and Linux endpoints in order to ensure there are no gaps in your data protection strategy. It does so by capturing and recording events at the system, user, and data levels, and allows you to fine tune responses based on these various factors. With SaaS deployment options and managed services, Fortra's Digital Guardian deploys rapidly and delivers fast results.
Enterprise DLP
These types of solutions can be deployed alongside data classification tools and software for managed file transfers (MFT), such as the Secure ICAP Gateway. During the process, adaptive DLP recognizes the different data classification labels and automatically enforces the appropriate policy and ensures labeling remains in place as the data moves throughout the network or leaves the organization.
Request a Live Demo
Incorporating email DLP into your cybersecurity portfolio is crucial. Talk to one of our experts to discover the DLP solution that's right for your organization.