Challenges and Threats of Domain Impersonation
Cybercriminals use domain impersonation for financial gain or sensitive data. This method of impersonation is gaining traction. According to Fortra’s 2023 Domain Impersonation Report , the average brand is targeted by 40 look-alike domains per month. Add this threat on top of the resource issues plaguing organizations and it’s no wonder impersonations can be difficult to stop.
The two common types of domain impersonation are look-alike domains and email spoofing.
Look-alike domains are domains nearly identical, or confusingly similar, but slightly altered and registered with intent to deceive.
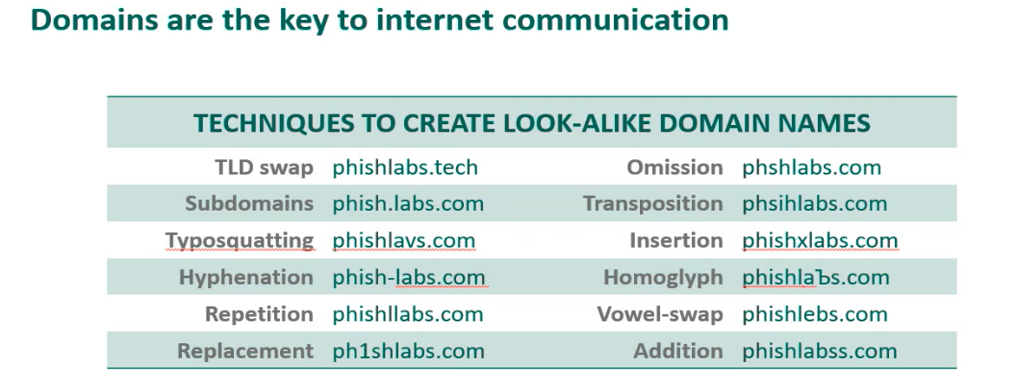
Email domain spoofing is one of the most common forms of cybercriminal activity and used in phishing and spam attacks. It doesn’t require a registered domain as it is a forgery of an email sender address.
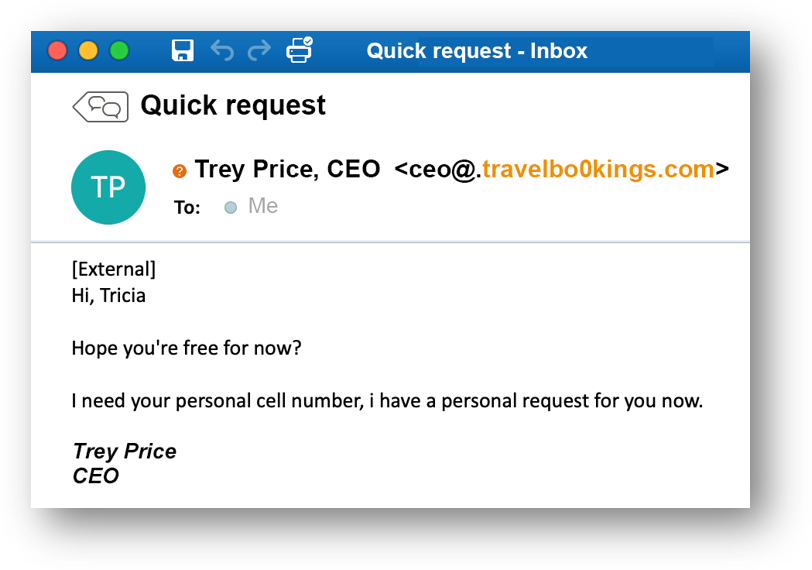
An email sent with a spoofed domain
Domain Impersonation Protection Products
DMARC protection for email authentication
Another way to combat impersonation is to implement DMARC reject on your email domains. When a cybercriminal uses your domain for email threats, they can mislead an organization’s customers causing long-term damage to the organization’s brand and customer trust. DMARC is an essential email authentication protocol that enables administrators to prevent hackers from hijacking domains for email spoofing, executive impersonation, and spear phishing. But email is complicated and getting email authentication correct is critical in blocking only the spoofed emails.
Domain monitoring
An organization should also consider domain protection from threats such as look-alike domains. Domains are vital to an organization and targeted by cybercriminals using look-alike domains for lucrative gains. In fact, Fortra's Domain Impersonation Report found the average brand is targeted by 40 look-alike domains per month.
However, resource issues make combatting look-alike domains challenging for an organization on their own. Having a solution that collects the data, curates the data, and mitigates with quick effective takedowns is essential for proper domain monitoring.
Stop Domain Impersonation

Organizations must make domain protection a part of their overall cybersecurity plan. However, the amount of work it takes to keep domains and sub domains safe can be more work than most can manage in-house. The scope of the domain service component includes detection, analysis, mitigation, and monitoring of domains for the following:
- Domains that contain brands or identified terms
- Being used in a “malicious” manner where the purpose is used to steal customer data, alter customer transactions, or exhibits other properties indicative of fraudulent activity.
- Being used in an “unauthorized” manner
Another part of combatting domain impersonation involves implementing DMARC reject on email domains. When a cybercriminal uses a domain for email threats, they can mislead an organization’s customers causing long-term damage to the organization’s brand and customer trust. Fortra DMARC Protection is an email authentication protocol that enables administrators to prevent hackers from hijacking domains for email spoofing, executive impersonation, and spear phishing.
Finally, takedown of malicious domains is needed for successful protection against impersonation. Fortra streamlines takedowns – takes immediate action on domains hosting phishing attacks. This will reduce corporate spend on defensive efforts monitoring/managing registrations.